Ain’t No Actor Trustworthy Enough: The importance of validating sources
KELA Cyber Intelligence Center
The list of ransomware victims has risen dramatically over the last few years. Due to the adoption of the “double extortion” tactic, companies now pay for data not being released and not only for the sole unlocking of computers. KELA is regularly monitoring ransomware gangs’ blogs where attackers announce their victims and leak data. Some actors are operating similar data leak sites though they do not necessarily use ransomware; they steal data through other means of infiltration and then threaten to release it or sell it to third parties or resell data stolen by other actors. In addition to that, some actors offer old or non-existing leaks and make fake and intimidating claims.
These offers have a direct impact on the cybersecurity landscape, generating extensive noise and preventing cyber threat researchers from focusing on real threats. Therefore, it becomes more important to validate sources before starting to follow them closely and accepting everything at face value. In this blog, KELA will share our process of reviewing new sources and assigning a level of threat, addressing sites such as:
- Amigos
- Coomingproject
- Dark Leaks Market
- Quantum
- Groove
Step 1 - Checking the Uniqueness of Offers
When a new site emerges, the question of how legitimate and unique is the data posted in it always pops. Sometimes it can be recognized almost at first glance: for example, when Amigos marketplace started to sell logs stolen from infected machines, KELA researched these offers. The analysis revealed that for most of the logs, the number per “stealer” malware was either the same number or awfully close to that of the older and more known “Russian Market” marketplace. Several “bots” chosen by KELA for comparison, were found to have the same content and the same ID – with the only difference being an added “v” to the ID. Finally, Amigos used the exact same UI and UX design, as Russian Market. Therefore, KELA concluded that this market is a scam.
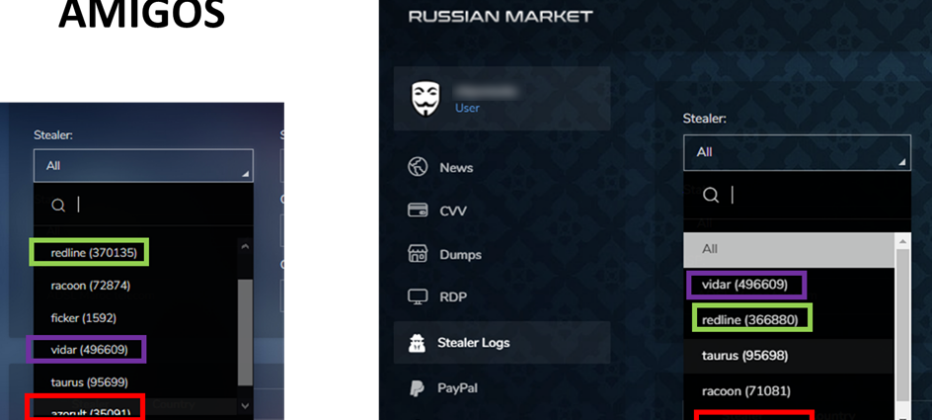
Comparison of offers on Amigos vs. Russian Market in July 2021
Now let’s take a look at Coomingproject – a data leak site that was launched in August 2021 and, in chatter on the XSS cybercrime forum, was claimed to be associated with ransomware. This case required more research to establish the site’s credibility.
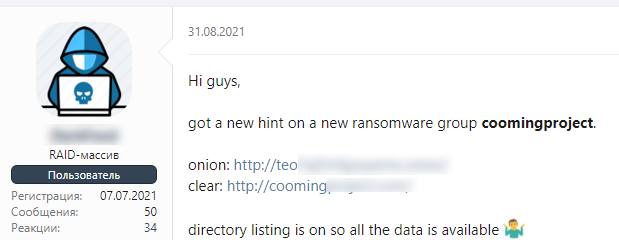
Chatter about Coomingproject on a cybercrime forum
Over the last two months, the site has published data of at least 36 companies and organizations worldwide, including Vimeo’s streaming service Livestream and Orange, a French telecommunication provider, which looked “promising” at first sight. The operators declared that they “attack all over the world”: “We are not a ransomware group we are like the shinyhunters group.” (ShinyHunters are an infamous hacking collective involved in multiple data breaches that affected Tokopedia, Zoosk, Minted, and others). However, it turned out these attackers fit neither a ransomware gang’s nor a hacking group’s profile.
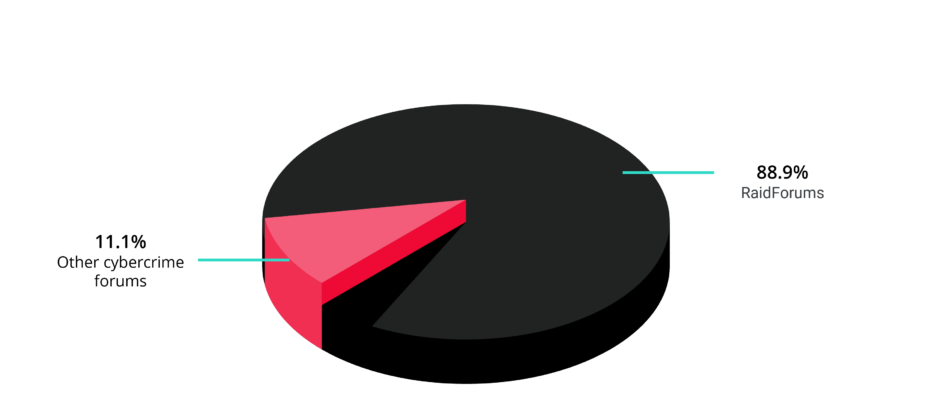
Despite the big names mentioned on the site, KELA’s research identified that all the leaks were old, with 88% of them being offered in the past on the cybercrime forum RaidForums. However, it does not instantly mean that all actors who are resharing or reselling old leaks are scammers – some collaboration may exist behind the scenes, which is why it is worth checking links between threat actors.
Step 2 - Checking Ties Between Actors
Threat actors are known to sometimes unite their efforts in order to intimidate their victims, gain maximum profit or maximum exposure. For example, Quantum blog, a recently launched data leak site dedicated to “the network security” as claimed by the actors, published two first victims in October. Upon KELA’s check, both victims were found to be previously hit by the DoppelPaymer and Xing ransomware gangs and published on their blogs. Analysis of data leaked by these ransomware gangs on these victims confirms that the same data was shared on Quantum. Moreover, for the Xing victim, the download link on Xing’s blog now also leads to the relevant page on Quantum. In this case, it is clear that some cooperation exists between those ransomware gangs and operators of the Quantum blog.
The actors behind Coomingproject, on the other hand, appear to be stealing leaks without any cooperation and tend to “target” specific actors. For example, a reputable RaidForums user who leaked data belonging to 10 victims of Coomingproject, complained that his leaks were “stolen” by Coomingproject’s actors and reshared on their site. Most of the leaks were indeed reposted on the same day or the following day on Coomingproject.
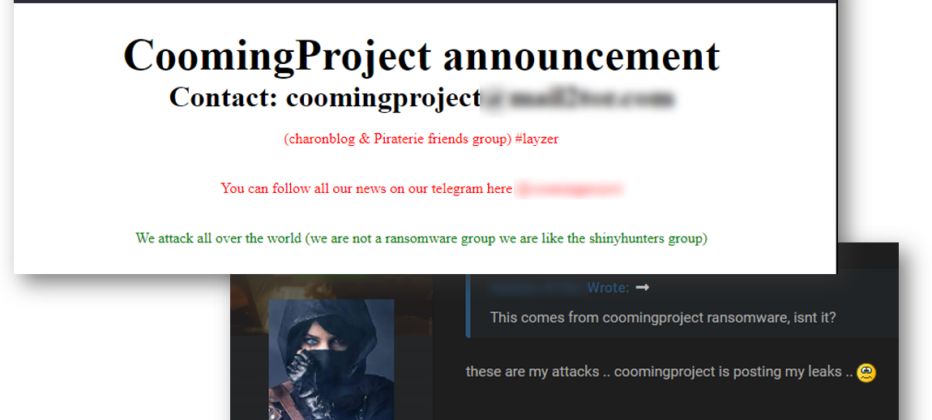
Coomingproject home page vs. claims of stolen data
With Coomingproject, as it turns out, the leaks were not unique and no collaboration with other actors was found; therefore, the actor behind this site cannot be considered as a high-profile actor. However, even if another actor passes these authenticity checks, it is still possible that they do not pose a real danger.
Step 3 - Understanding the Actor’s Credibility
Dark Leaks Market is a site that claims to exist since 2017; the actors behind the site have started to actively promote it in December 2020. The actors do not pretend to sell information stolen by them but rather claim to resell the data at the lowest price: “We have bought the databases from the original leakers to resell on our Dark Leak Market.” The market even sells samples of stolen data – a suspicious act in the cybercrime community, where samples are usually released for free.
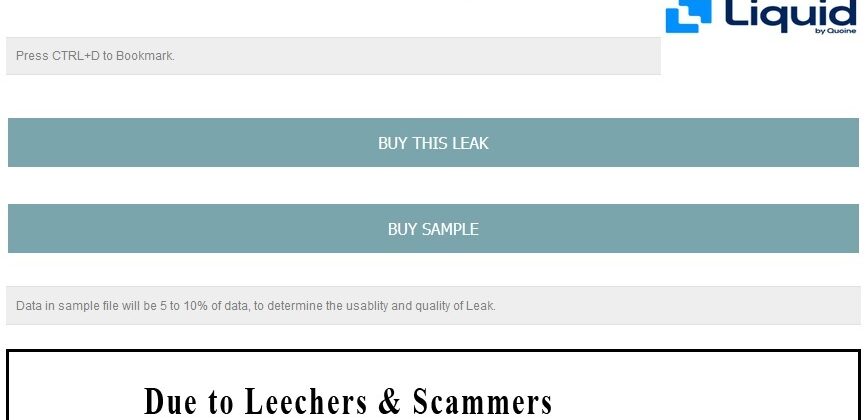
Alleged data of Liquid Global, a cryptocurrency exchange that suffered a data breach, listed on Dark Leaks Market
At a closer look, Dark Leaks Market is hardly a source that is able to provide valuable information. Several offers on the site were found to be previously leaked for free or even do not exist in public access. For example, alleged data of IDFC First Bank was first shared on the Everest data leak blog as proof of a successful attack. Moreover, IDFC First Bank did not confirm the attack, which raises doubts as to whether this data leak even existed in the first place.
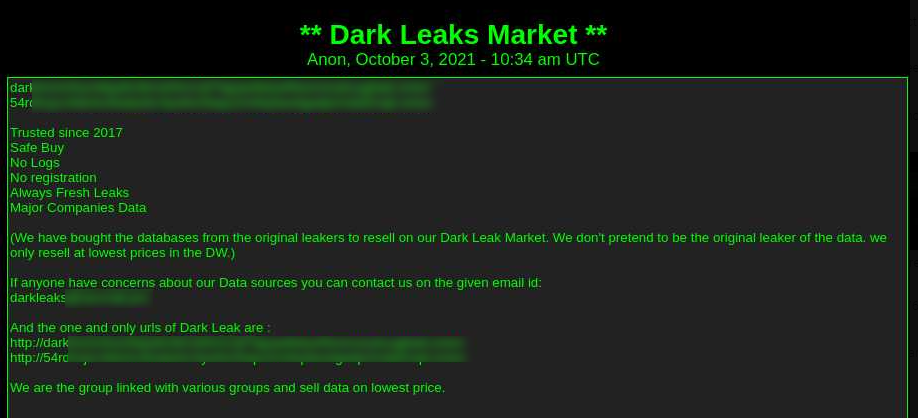
Advertisement of Dark Leaks Market on a paste site
It looks like Dark Leaks Market follows the demand created by news disclosing big data breaches; Air India and Domino’s India were reported to be affected by data breaches – and then this data was listed for sale on Dark Leaks Market. Since it was posted only after the news came out, actors behind Dark Leaks Market do not look to be connected to the original attackers – otherwise, they would have offered data for sale before it was reported. Cybercrime chatter adds other doubts about the site’s content: some users confirmed it does not sell legitimate data.
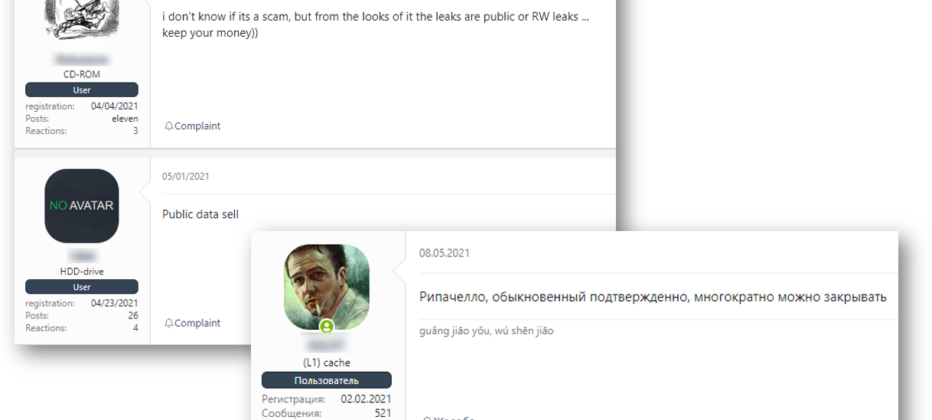
Different users, including an XSS former moderator, claim that actors behind Dark Leaks Market are scammers. The post in Russian says: “A usual ripachello [scammer], it was confirmed multiple times, [the thread] can be closed.”
The most recent example is the Syniverse breach, whose data was listed on sale on Dark Leaks Market a few days after the data breach made it to media outlets. The actors offered to sell it for USD500, which is another hint to scam since such a database would be priced higher if it was real.
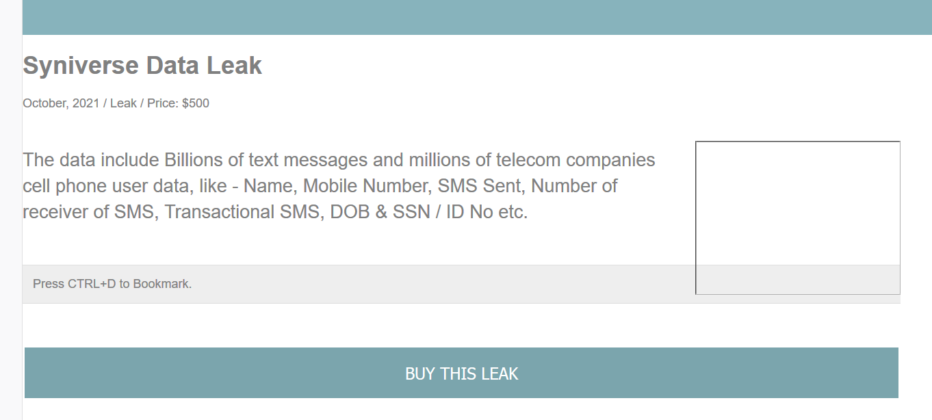
Alleged Syniverse data on sale on Dark Leaks Market
Step 4 - Always Question the Actor’s Claims
Even if the source and the actors behind it pass all checks, the motto of a researcher is “trust no one.” A source’s credibility can be overturned with any suspicious activity observed. As such, KELA has been closely following threat actors behind the cybercrime forum RAMP launched in July 2021. One of the outcomes of the events around the Babuk ransomware operation and RAMP was a site called Groove. RAMP’s former administrator claimed to maintain a financially motivated group named Groove, which does not have its own ransomware product, but still targets companies and steals their data. 10 days after Groove’s site was launched and some questionable victims were published, an XSS user identified by KELA as the same actor (RAMP’s former administrator), claimed that he started working on an article for this forum dedicated to manipulating journalists and researchers.
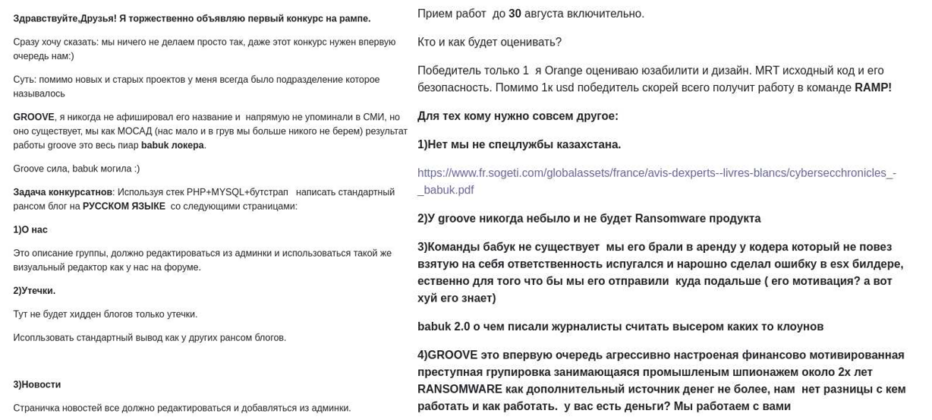
On August 23, 2021, the actor behind Groove announced a competition of web developers whose task was to create a “standard ransom blog” in Russian for Groove. The winner would get USD 1000 and “possibly a job in the RAMP team.” Alongside the competition requirements, the actor claimed that Groove is a financially motivated group that has been engaged in industrial espionage during the last two years and never had their own ransomware
The actor also made it specifically personal with several security researchers – including KELA: first, the actor has changed his profile picture on RAMP to that of one of KELA’s VPs, and included their name; and then he publicly declared his willingness to grant only one interview – and specifically to that VP. Needless to say, this has raised our suspicions even more and we did not engage the actor and his grandeur ideas.
In early September, Groove posted a message titled “We can just agree” where it was suggested that Groove wants USD30 million to cease their activity. The readers were invited to transfer the money right away. In October, this time on RAMP, this actor started a thread, offering to “do stuff that the others don’t”. In the offer, he claimed to be willing to target US government institutions and the medical sector, as well as certain European countries, apparently in response to US counter operations and other ransomware groups staging away from government and healthcare targets.
Moreover, reacting to the shutdown of the REvil ransomware operation, the actor claimed on Groove that his gang will start targeting not only western companies but also Russian ransomware affiliate groups. It was also claimed that Groove will switch to a WordPress site, “so it will be hot and with comments”. The next announcement called for all the affiliate programs to stop their infighting and focus on attacking the US government sector but avoid attacking China.
Ultimately, on October 22, the actor behind Groove revealed that the site is just a “trolling” project, aimed at manipulating the western media and exploiting people’s fear of ransomware groups. It was claimed that there is no such thing as the Groove gang and that one person was behind the whole affair, who has worked with many ransomware affiliate programs, including BlackMatter, LockBit, and others. The author claims he decided to write an article about mass media manipulation, and the Groove site was created just for that. Lastly, the same actor has posted on the XSS forum, bragging about the successful campaign designed to manipulate media and researchers.
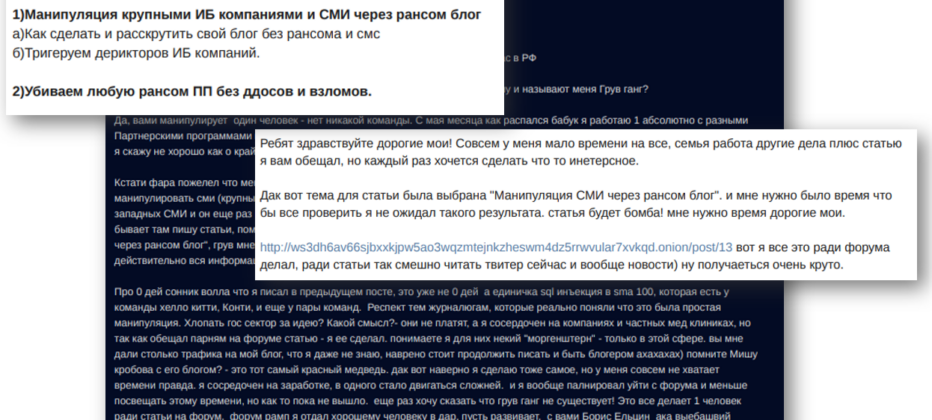
The actor behind Groove announces that the Groove operation does not exist – and he is the one person responsible for the site. Simultaneously, the same actor on XSS tells the identical story
While the actor still seems to be a real participant in different cybercrime schemes and ransomware operations, this incident showcases how crucial it is to doubt all claims of cybercriminals before defining their credibility and level of threat. In this case, is it not clear if the “Groove operation” was a hoax from the beginning or if this revelation is another level of manipulation from the same actor. Most of the messages were later deleted from Groove, leaving only announcements of victims; and the site has been down for several days.
Conclusion
Data breaches are one of the major concerns of companies and organizations worldwide. Organizations are required to follow regulations to protect personal data. Threat actors take advantage of that, aiming to put their hands on sensitive data and by that on people’s money. They sell, trade, and auction extorted corporate data, aiming to increase their profit.
Actors that re-share old data leaks and sell non-existing data prevent enterprise defenders from focusing on real threats and security risks. Therefore, as much as we always recommend monitoring cybercrime sources in order to prevent attacks, we also urge defenders to perform necessary due diligence before raising the alarm:
- Check how unique the contents of a new source are
- Perform investigation about the actors behind the source
- Identify ties between these actors and existing actors
- Re-assess conclusions and assigned level of threat while monitoring a source
