How the Cybercrime Landscape has been Changed following the Russia-Ukraine War
Elena Koldobsky, Threat Intelligence Analyst
On February 24, 2022, Russian forces invaded Ukraine, following years of tension between the two countries. The notion of war led multiple countries to speculate that Russia may use cyber attacks against Ukraine and supporting it western organizations and companies, with the US sending “top security officials” to help NATO prepare for Russian cyberattacks. Surprisingly, expectations for severe cyber-attacks on Ukraine and Europe turned out to be overestimated, as Russia refrained from large-scale attacks, and instead used distributed denial-of-service and wiper attacks on Ukrainian governmental institutions, infrastructure and telecommunications companies, and more. To defend itself, Ukraine raised a volunteer “IT Army”, which, together with hacktivists organizations from across the world, is targeting Russian companies and organizations to this day.
The winds of change have not passed over the cybercrime underground. From new illicit services that have never been available before, through war-related discussions appearing on apolitical cybercrime forums, to a hacktivist group using a famous Russian ransomware gang’s source code to target Russian companies – the cybercrime landscape has altered beyond recognition.
This report reviews the various changes that occurred in the cybercrime underground following Russia’s invasion of Ukraine. It provides a unique window into the delicate geopolitics of cybercrime, demonstrating how real-life emergencies influence services and opportunities and generate new trends.
The emergence of new services
The cybercrime underground is known for offering services that are usually considered to be illegal, sometimes immoral, and often otherwise unobtainable. Among the ‘traditionally’ offered non-cyber-related services and products are hitmen for hire, organ trading, weapons, drugs, and more. However, with new restrictions and prohibitions stemming from the war between Russia and Ukraine, a new line of previously unseen services has emerged, such as transportation out of Ukraine. Interestingly, many of the requests emerging following the war were detected on hacking-related forums and not the “traditional” markets offering physical goods and services. The existing cyber-related services (purchasing VPN illegally, for example) are also adapting to new needs and users.
Transportation out of Ukraine
On February 24, 2022, mere hours after Russia’s invasion of Ukraine has begun, the State Border Guard Service of Ukraine announced that due to martial law, Ukrainian men between the ages of 18 to 60 are banned from leaving the country. The desire to depart a war zone, along with the wish of many men to flee with their loved ones to safety, has led to a previously unnecessary need – the means to cross the border of Ukraine.
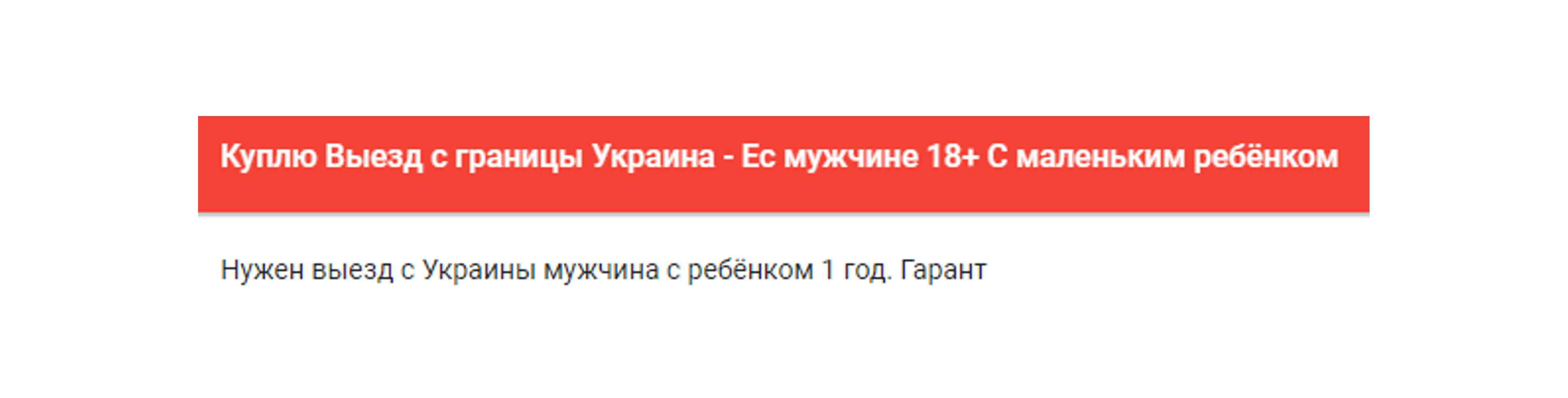
The actor wwostok55 stating on the Russian-speaking forum Dublikat that he will purchase an exit from Ukraine to EU for a male aged 18+ with a year-old child, as seen on KELA’s Cybercrime Intelligence platform
Although requests to assist in leaving the country were seen mainly during the beginning of the war, individuals stranded in Ukraine are seeking means to cross the border to this day.
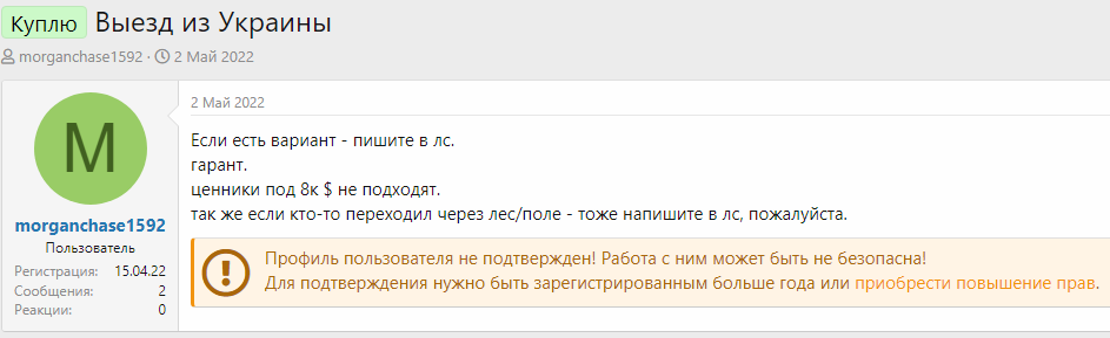
The user morganchase1592 asking on the Russian-speaking forum Dublikat for ways to depart from Ukraine. “If it’s possible – DM me. Guarantee. Price under 8k $ does not fit. Also, if someone crossed through a forest / field – also DM me please”, posted on May 2, 2022.
With the emergence of the demand, the supply was soon to arrive, and various actors previously engaged in credit card scams and fraudulent activity were detected offering passage through the border.
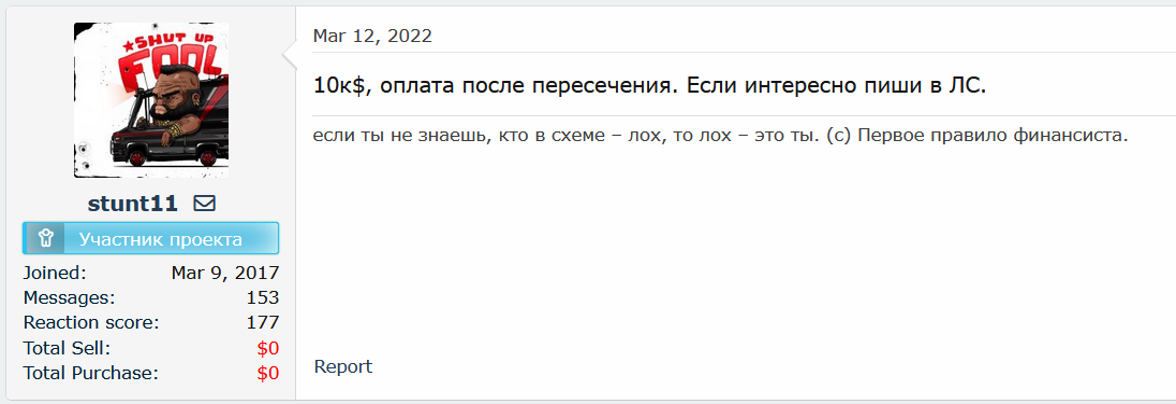
The actor ‘stunt11’, who was previously detected seeking used US or EU credit cards, is offering a passage across the border for “10k$, payment after crossing. If interested DM me”.
On April 29, 2022, the user Kuklus_One71, posted a statement on the Russian-speaking forum WwhClub offering “departure from Ukraine for men”. The user indicated that they are assisting men in leaving the territory of Ukraine through the fields, either by using a map and coordinating with the border guard to let the client pass or by a guide who will lead the way – which will be more expensive.
The user Kulkus_One71 offering service to cross the Ukrainian border
Demand for money transfer services
Centuries of social, political, economic, and cultural bonds between Russia and Ukraine, stemming from the countries’ shared border, Soviet policies of migration within the Soviet Union, and policies introduced during the existence of the Russian Empire, resulted in vast connections between the peoples of both countries. Relatives and friends often reside on different sides of the Russia-Ukraine border, and businesses operate on both sides of said border.
With the beginning of the invasion, Russia passed a series of laws forbidding citizens from providing any financial, material, or technical support to foreign states or organizations, or their representatives. According to the new legislation, providing such support would be considered an action against the security of the Russian Federation, and it is punishable by imprisonment for up to 20 years. Similarly, Ukraine has banned money transfers from Russia and Belarus and transfers in Russian and Belarusian rubles. As a result, Russian citizens can legally no longer provide financial support to their relatives and friends in Ukraine or conduct business with Ukrainian citizens or entities. Hence, they are searching for alternatives to transfer money from Russia to Ukraine.
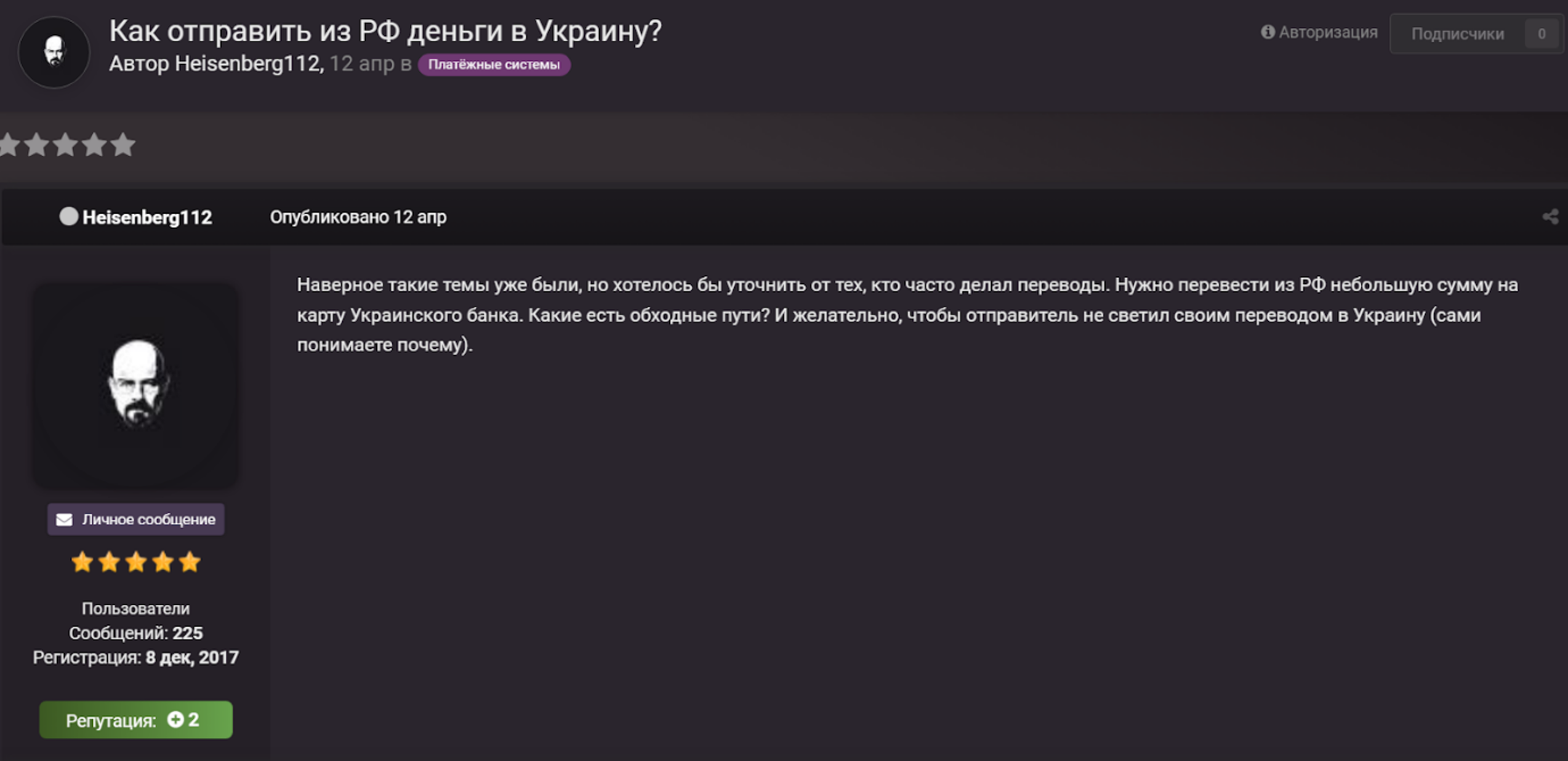
On April 12, 2022, the user Heisenberg112 asked users of the Russian-speaking carding forum CCCC for means to transfer money from Russia to Ukraine
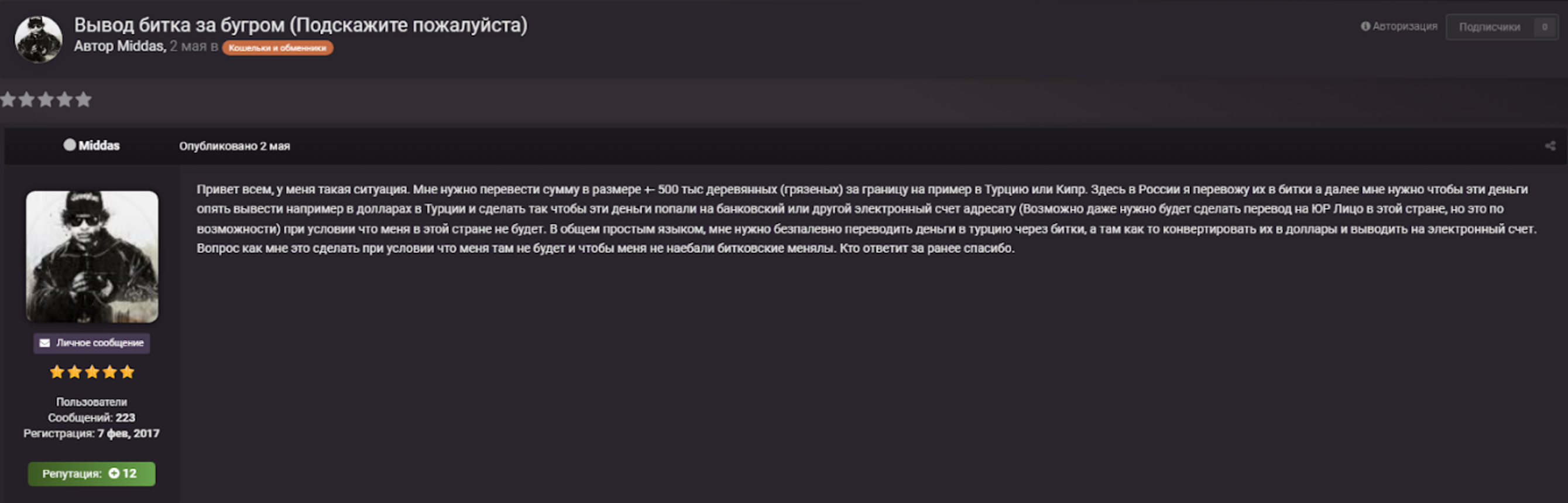
Moreover, on March 1, 2022, Russia issued a decree banning individuals from transferring over 10,000 USD or the equivalent in another currency from their account in a Russian bank to their account abroad or to another person abroad during one month (as of now, the limit has been raised to 150,000 USD). As a result, many Russian individuals eager to flee the country with their savings are turning to cryptocurrency to transfer money out of the country.
On May 2, 2022, the user Middas published a query on the forum CCCC, stating that he needs to transfer nearly 500 thousand Russian rubles to Turkey by first exchanging it to bitcoin in Russia, and then exchanging it to USD in Turkey. The user asks how he can do it without being “screwed” by bitcoin exchangers.
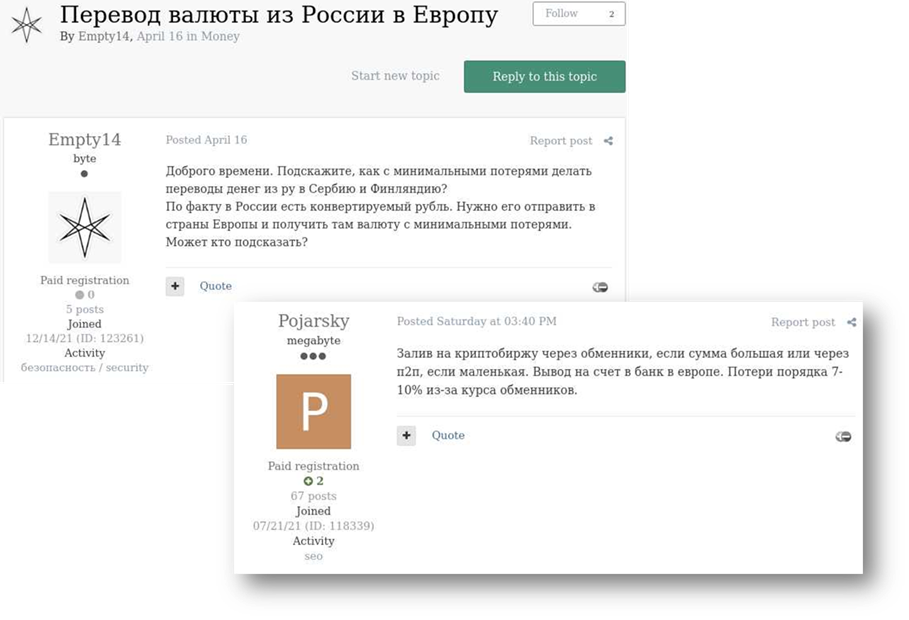
On April 16, 2022, the user Empty14 posted a question on the Russian-speaking hacking forum Exploit asking how to transfer money from Russia to Serbia or to Finland. Multiple users suggested exchanging the money to cryptocurrency and using peer-to-peer (P2P) crypto exchanges.
Along with internal restrictions imposed by Russia, global sanctions have also influenced the way individuals transfer money to Russia. The European Union and its allies have suspended multiple Russian banks from Swift, an international payment system allowing rapid transfer of funds across borders, which harmed their ability to operate globally. Additionally, the Western Union payment system has announced that they are stopping money transfers in Russia and Belarus starting from March 24. Other companies such as Wise, Remitly, Visa, and Mastercard added their own restrictions, making money transfers to Russia nearly impossible. As a result, those who wish to transfer money from abroad to Russia often seek alternative ways via cryptocurrency exchanges and often address the cybercrime underground for information.
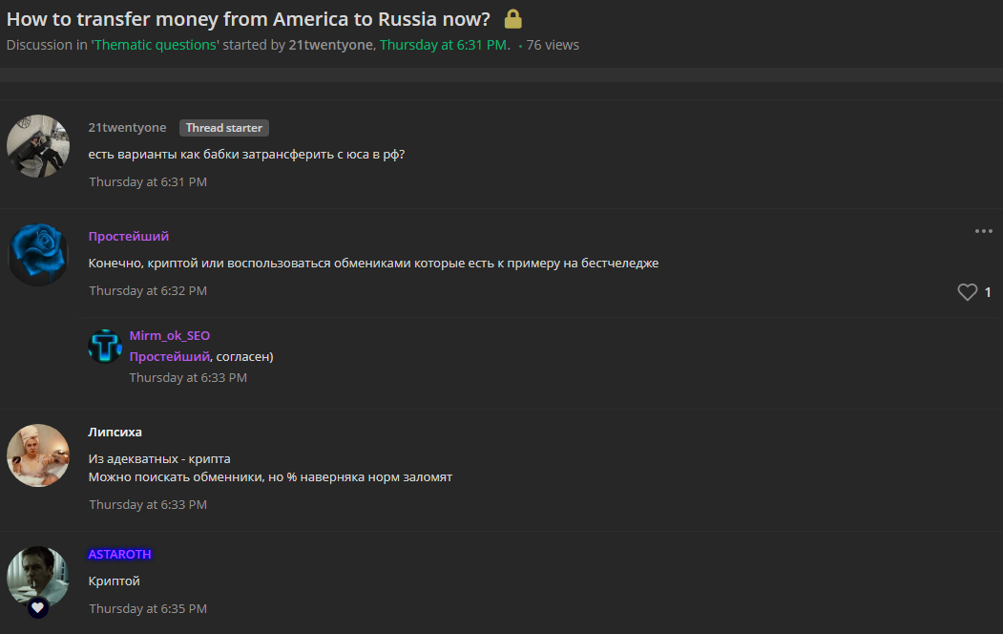
On May 5, 2022, the user 21twentyone posted a question on the Russian-speaking forum lolzteam, asking how to transfer money from the US to Russia. Many of the replies suggested doing so using cryptocurrency.
Money transfers are essential not only to naïve, law-abiding citizens, but also for cybercriminals. For years, Russia was known for turning a blind eye to the illicit dealings of its cybercriminals, as long as their targets were outside of Russia itself, turning Russia into a “cybercrime heaven”. However, Russia’s attack on Ukraine and the global attempt to isolate Putin, resulted in sanctions on cybercriminals as well.
For instance, on April 5, German law enforcement and the US Justice Department, shut down Russia’s largest cybercrime marketplace, known as Hydra. In addition, on April 3, 2022, the US Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned over 100 cryptocurrency addresses that were related to Russian cybercriminal activity. The virtual cryptocurrency exchange Garantex was also sanctioned for facilitating illicit transactions with cybercriminals. These sanctions affect cybercriminals’ ability to exchange cryptocurrency obtained through illicit activities into other currencies. It is thus driving criminals to seek alternative means to sell their goods and transfer their illegally obtained money.
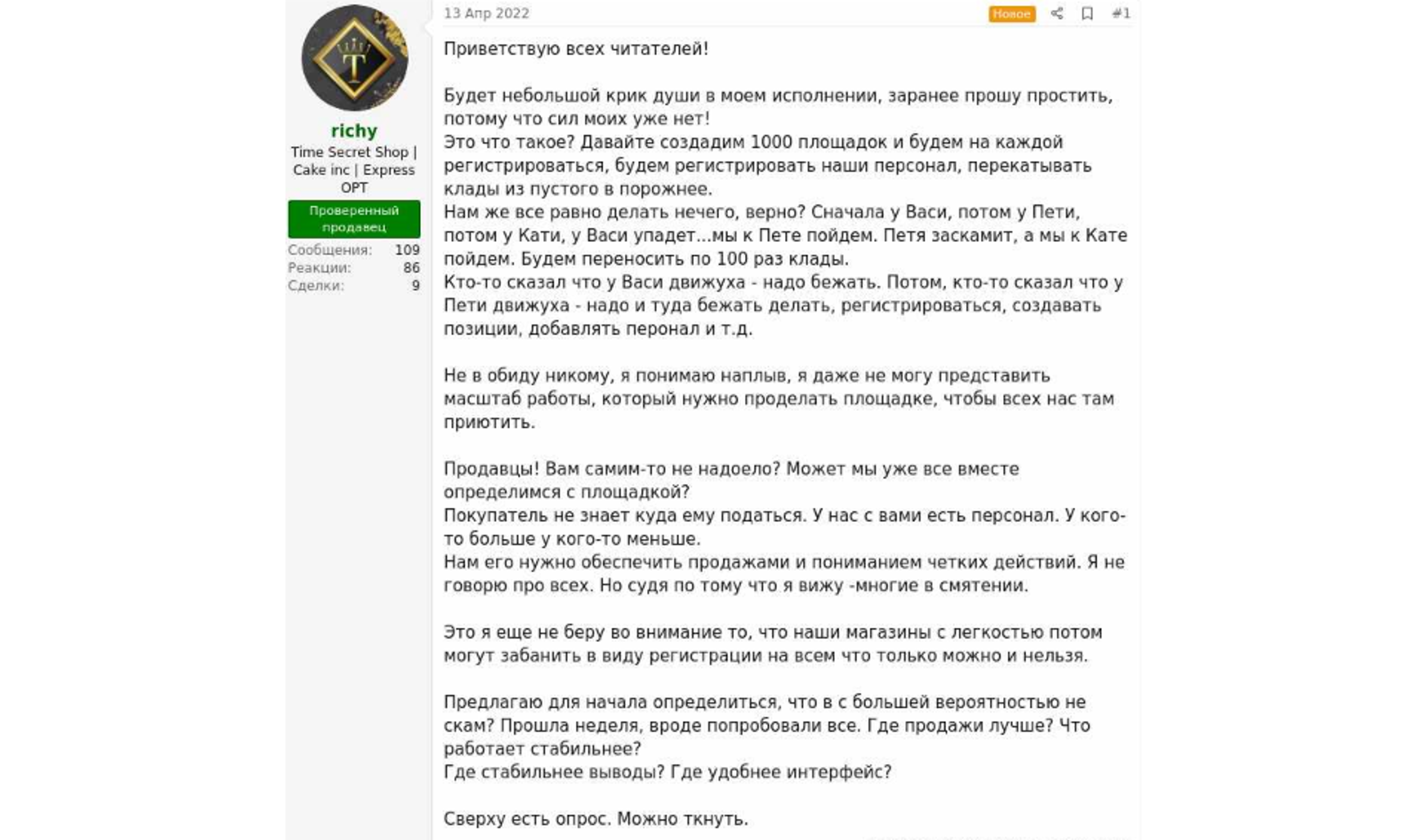
On April 13, 2022, the user richy published a post on the Russian marketplace-forum RuTor, suggesting finding an alternative to the now-closed Hydra. The post raised massive discussions on what the alternative platform should be and if such a platform should indeed be created.
While many seek methods to transfer money, for the time being KELA could not identify such services being offered on the cybercrime underground. Instead, actors often recommend other users to address legitimate channels, such as cryptocurrency exchanges. However, such services may likely appear in the future, for instance, if sanctions are imposed on cryptocurrency exchange in Russia, actors may need to address alternative services to transfer money.
VPN services
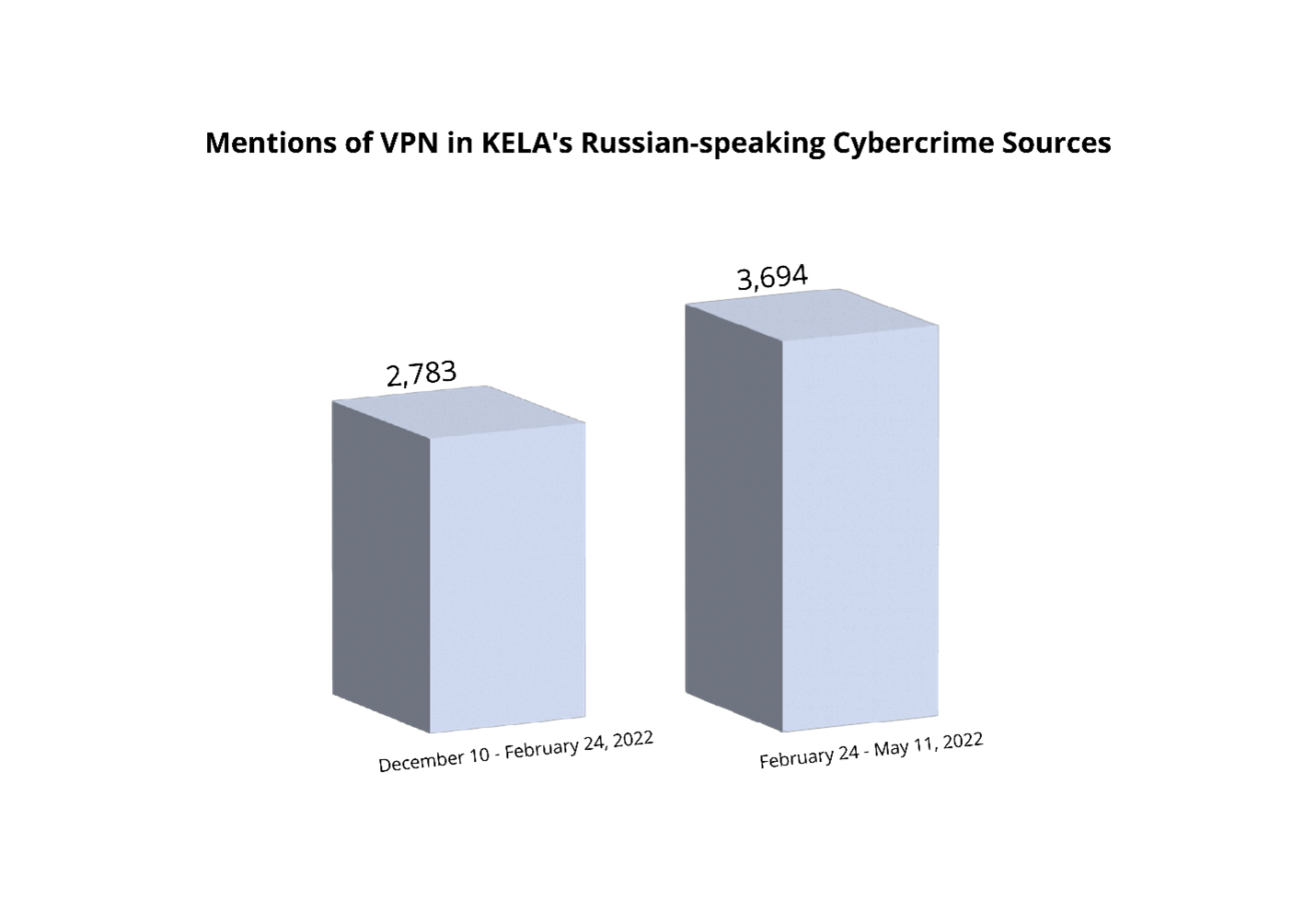
With the beginning of the invasion, Russia passed censorship laws over the war, including new legislation that envisions up to 15 years in prison for organizations distributing “fake news” about the war, calling it “war” included. Meta products Facebook and Instagram were banned. As a result, demand for VPN services in Russia grew by over 1,000%.
KELA has observed a spike in mentions of VPN services in its Russian-speaking sources during the time period between the beginning of Russia’s invasion of Ukraine (February 24, 2022) and May 11, 2022, compared to the number of mentions of VPN in a similar time period prior to the war, from December 10, 2022, to February 24, 2022.
Due to the nature of the activity prevailing in the cybercrime underground, it is safe to assume that the vast majority of its users are familiar with VPN services. The spike can be caused by the arrival of new users hoping to acquire accounts for reliable VPN services, especially since Russia has started to block URLs linked to some of them, while legally paying for remaining VPNs is hard without having non-Russia issued Visa and MasterCard credit cards.
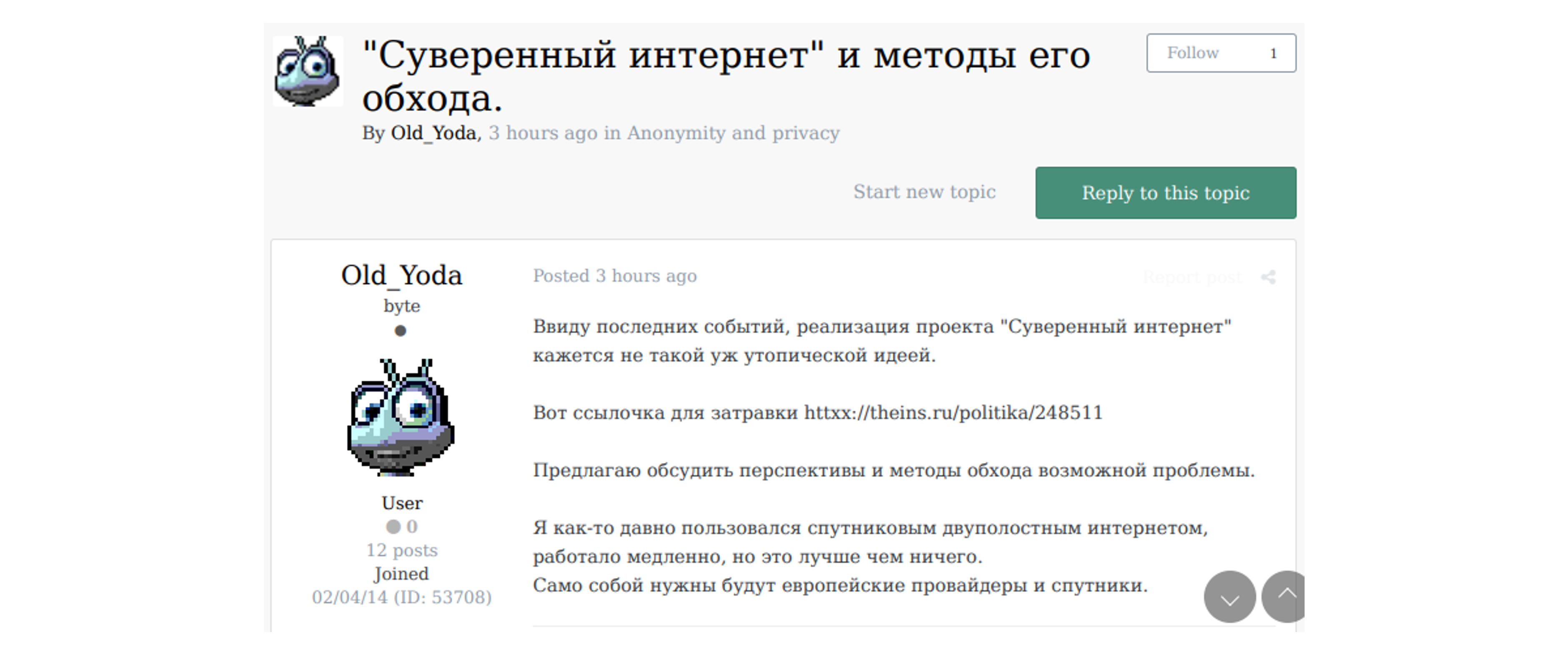
On March 11, 2022, the user Old_Yoda posted a message on the forum Exploit saying that Russia’s Sovereign Internet project (a series of laws passed in 2019, aiming to disconnect Russia from the World Wide Web) appears to become reality, and proposes to discuss methods to bypass the issue. The post raised a discussion concerning the various VPN services that are either available or blocked in Russia.
Malware, forums, and ransomware
Former Soviet Union countries are considered to be cybercrime hotspots, due to low rates of prosecution and conviction of suspected cybercriminals. Although Russia is known as the most prominent among these “cybercrime heavens”, Ukraine is also high on the list. Therefore, it was only natural that Russia’s invasion of Ukraine would have a certain impact on cybercriminals residing in Ukraine.
Raccoon Stealer shutting down
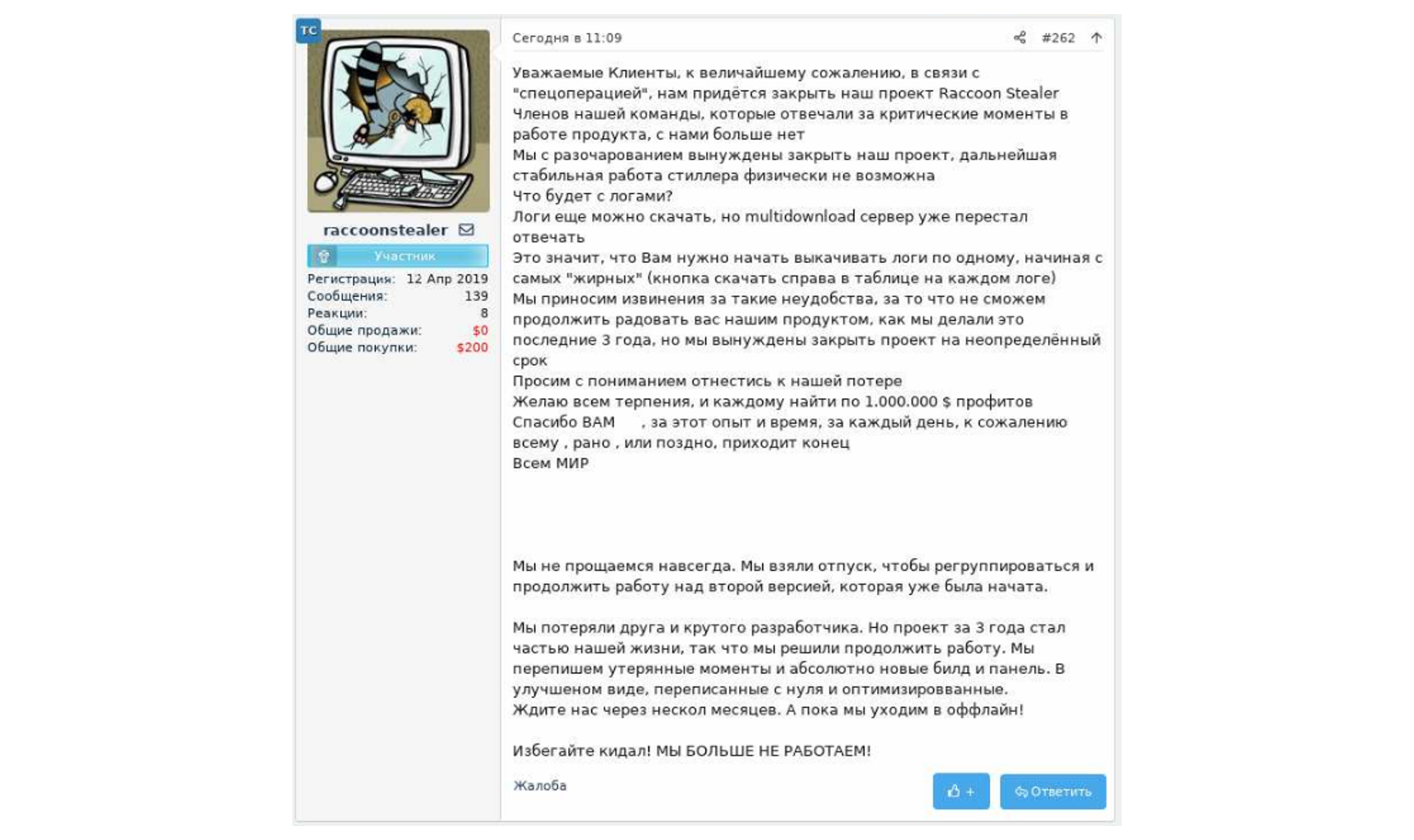
One of the groups affected by Russia’s invasion of Ukraine was the one operating the Raccoon Stealer malware. Raccoon Stealer is an information stealing trojan distributed as malware-as-a-service, for USD 75 per week or USD 200 per month. Subscribing to the service would grant threat actors access to an admin panel that allows them to customize the malware, retrieve stolen data and create new malware builds. Due to the malware’s capabilities of stealing a wide range of information, it was highly popular among threat actors. However, on March 2, 2022, the actors behind the malware uploaded a post on several Russian-speaking hacking forums, stating they are suspending their operation because their core developers were “no longer with them” due to a “special operation”. Possibly they have been killed in Ukraine.
“Dear Clients, unfortunately, due to the “special operation”, we will have to close our project Raccoon Stealer. The members of our team who are responsible for critical moments in the operation of the product are no longer with us. We are disappointed to close our project, further stable operation of the stealer is physically impossible.” (Translated)
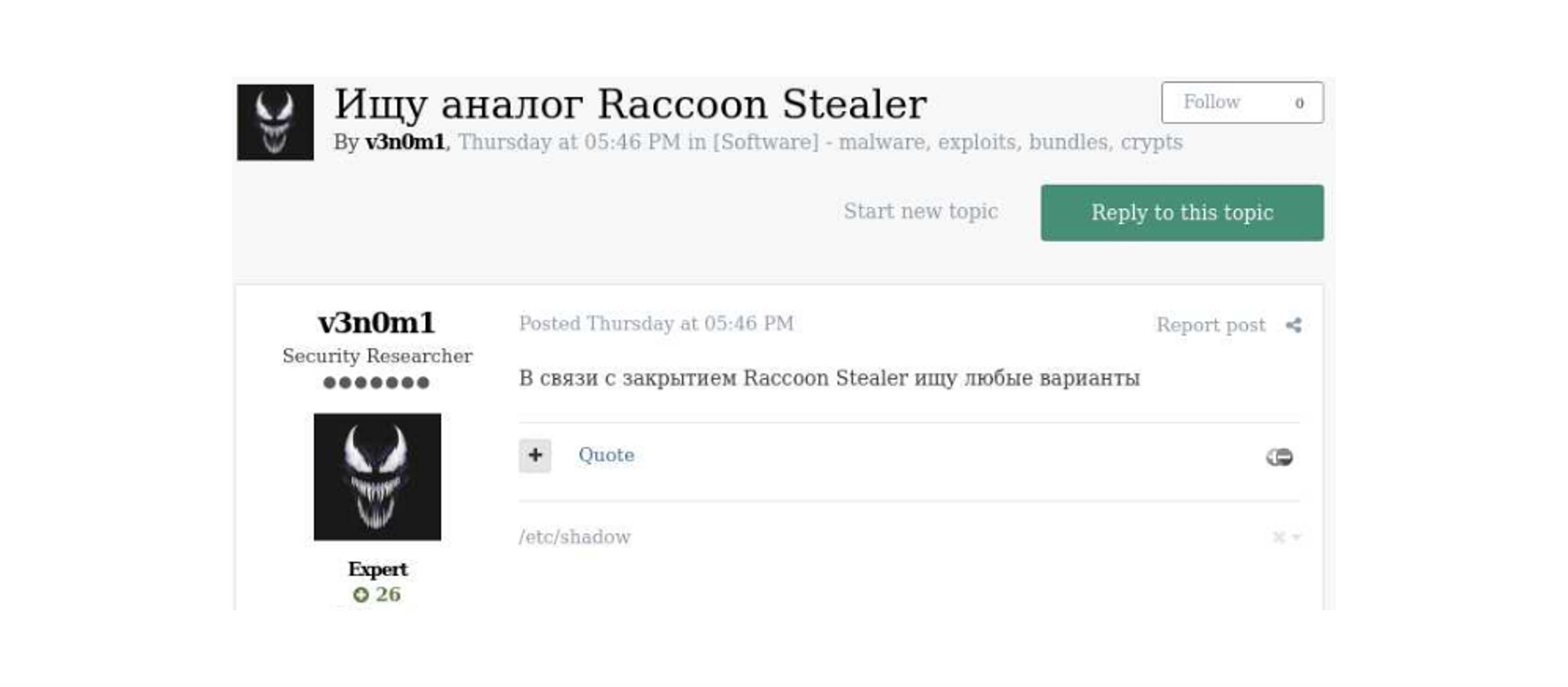
Due to the suspense of Raccoon Stealer’s operation, threat actors appeared to be migrating to the Mars Stealer operation, which offers similar services as Raccoon Stealer. Another stealer suggested as an alternative is Vidar. On June 2, 2022, the actors behind the Raccoon Stealer claimed they returned with version 2 of their malware. The malware is still in the test process but the actors expect to bring their old customers back after the release.
On April 7, 2022, the user v3n0m1 posted on the forum Exploit: “Searching for an analogue for Raccoon Stealer. Following the termination of Raccoon Stealer, I’m searching for any variant”
XSS is no longer a united FSU forum
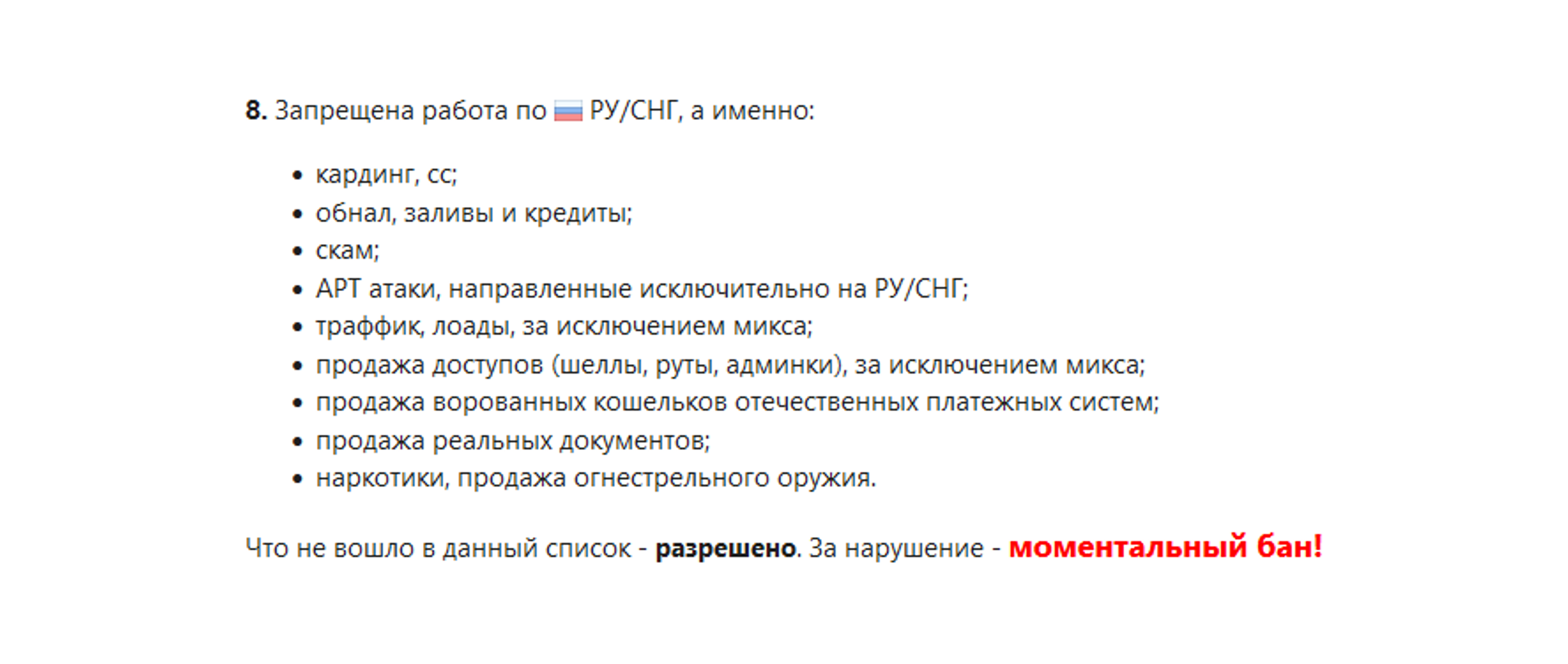
XSS is a popular Russian-speaking cybercrime forum created to share knowledge about exploits, vulnerabilities, malware and network penetration. For years, the forum’s rules have prohibited users from discussing politics, mainly “racist, national, political and religious propaganda”, and illicit activity in Russia and the Former Soviet Union (FSU) was not allowed.
The forum rules as seen on XSS
However, KELA recently observed an increase in conversations where users debated whether attacking Ukraine is acceptable, stating that Ukraine is a western country. This shift demonstrates a change in Russians’ perception of Ukraine that comes across not only in mainstream media but in cybercrime forums too.
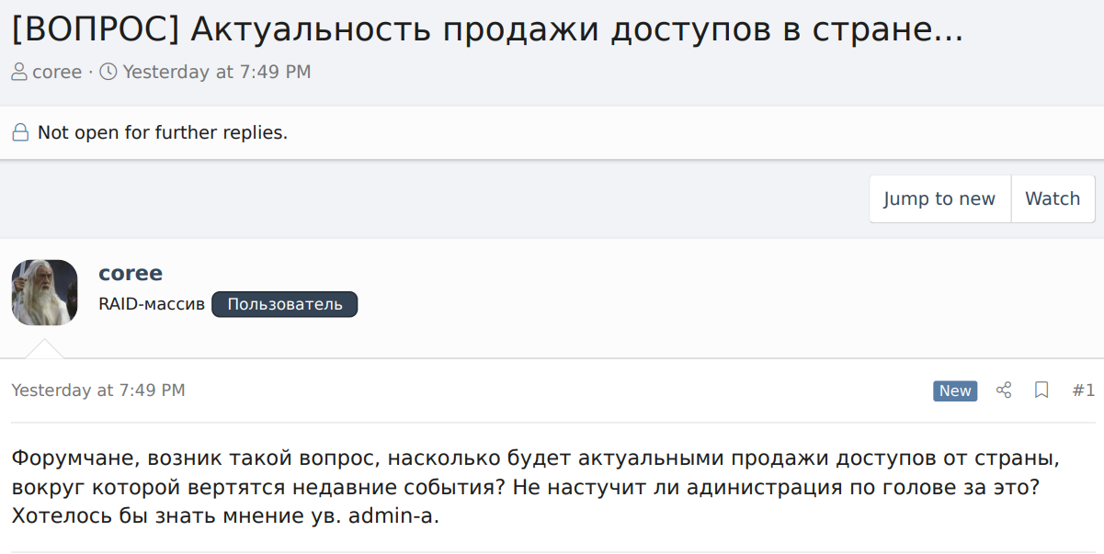
“Forum-mates, I’ve got a question – how relevant would it be to sell accesses to a country, that is involved in recent events? Would the administration be mad for that? I’d like to know the admin’s opinion.”
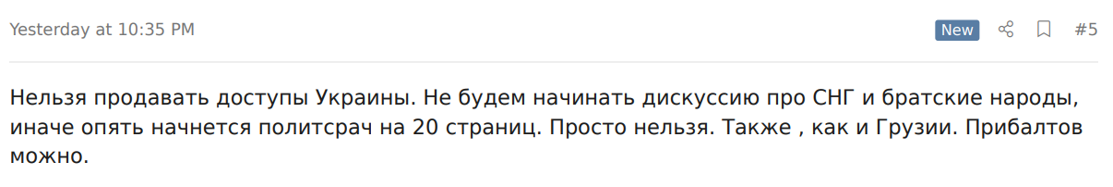
XSS moderator ‘coree’ replied “Selling accesses to Ukraine is not allowed. We will not start the discussion on FSU and brotherly nations, or else a political discussion of over 20 pages will start. It is simply forbidden. Same goes for Georgia. Baltic states are allowed.”
Ransomware and similar groups choosing sides
Following Russia’s attack on Ukraine, several ransomware groups publicly announced their support to either of the countries or chose to remain neutral.
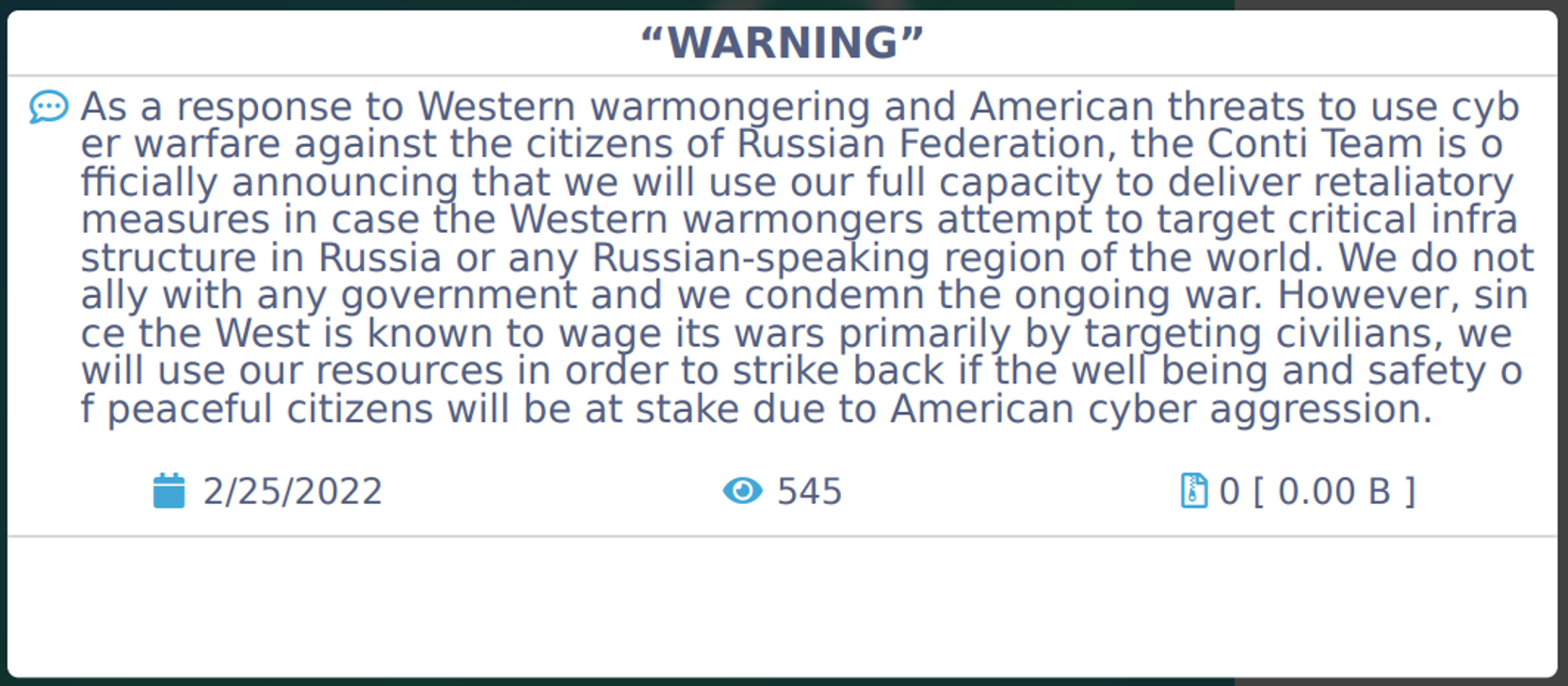
For example, Conti announced their support of the Russian government and threatened to attack the infrastructure of anyone targeting Russia’s infrastructure. Conti is a Russian-speaking Ransomware-as-a-Service (RaaS) operation which is believed to be a successor of the Ryuk ransomware operation. Ransom payments received from using Conti are divided between the affiliates directing the attack and the Conti managers. The group’s affiliates often breach target’s networks after infecting corporate devices with BazarLoader or Trickbot malware, which provide remote access to the compromised system. The group and its affiliates do not target Russian companies and can therefore, allegedly, operate freely within Russia.
Shortly after the announcement, on February 27, 2022, a suspected Ukrainian researcher leaked the internal conversations of its members. In April 2022, Conti’s source code which was shared in the leak too, was used by a hacking group known as NB65 to breach Russian entities, steal their data and leak it online as a response to Russia’s invasion of Ukraine.
Conti is stating their support of Russia on their data leak site
Interestingly, Conti’s rhetoric towards the war between Russia and Ukraine appears to have changed in recent months. In a post uploaded on March 31, 2022, the Conti group compares itself to Kiev by stating that “this is the second month of this occupation within two days”. The group implied they did not shut down immediately after their internal information was leaked (in the same way Russia planned to complete the invasion of Kiev in two days but failed).
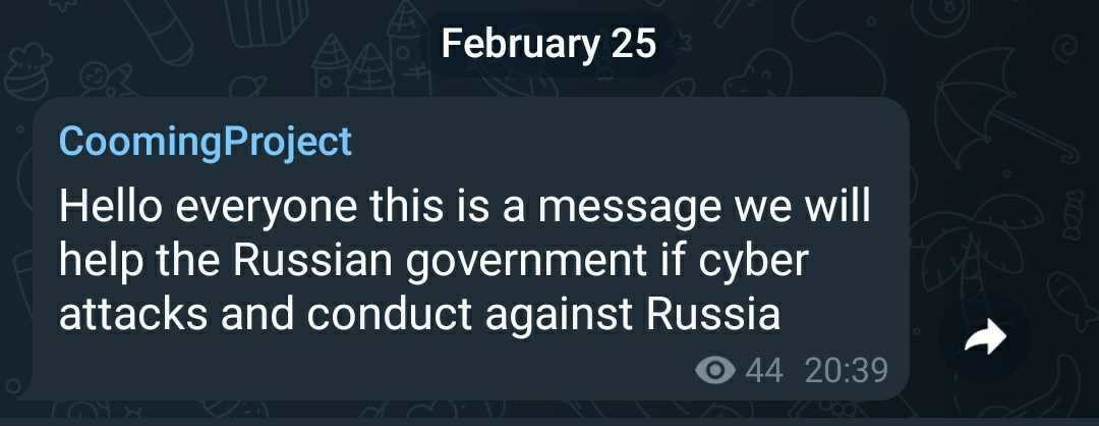
Another group choosing to support Russia is the CoomingProject group – a data leak site that was claimed to be associated with ransomware (though discovered by KELA to fit neither a ransomware gang’s nor a hacking group’s profile). The group published an announcement on February 25, 2022, stating that they “will help the Russian government” if cyber attacks are conducted against Russia. In response, on February 27, 2022, the hacking group AgainstTheWest, which usually targets government and corporate entities tied to the Chinese Communist Party, claimed to have attacked CoomingProject, calling them “a team of 6 French-based teenagers and young adults”. The group also claimed to have attacked various Russian companies.
The CoomingProject group is announcing their support of the Russian government
Other ransomware groups preferred to refrain from picking sides. The LockBit ransomware group, for instance, stated on February 27, 2022, that they will remain neutral, as they “are all simple and peaceful people”, and that for them “it’s just business”. In addition, the group stated that they “will never, under any circumstances, take part in cyber-attacks on critical infrastructures of any country in the world”.
Another group choosing neutrality was ALPHV (also known as BlackCat) ransomware group. On February 28, 2022, a team member of the ransomware group ALPHV published a message via an internal support chat, claiming that they “categorically condemn Conti and any other people or groups” for introducing politics to their “common ecosystem”. The group stated that the “Internet, and even more so its dark side, is not the place for politics”.
Conclusion
Russia’s attack on Ukraine forever changed the lives of those involved, with thousands dead and millions fleeing the country. We often think of the cybercrime underground as a parallel realm of sorts that has no interface with the simple life of most people. However, major changes in the world appear to affect the landscape within the cybercrime forums and community in a manner similar to their influence on the lives of naïve, law-abiding citizens, who are at times have no choice but to turn to now-illegal services to perform actions that only a while ago were considered to be mundane and simple. Such is the case of those desiring to leave Ukraine or receive money from their Russian friends, and of Russians wishing to speak of the war, transfer money or flee their motherland. Although they are often perceived as untouchable, hackers, threat actors and cybercriminals are also affected, and may even find their death in war.
Understanding global trends, being familiar with the world changes, and staying updated on global issues allow better identification of threats and alterations in the cybercrime underground. KELA’s comprehensive platform facilitates diving into the cybercrime underground and conducting deep analysis and intelligence investigations based on real-time data obtained from hard-to-reach, dynamic internet sources. Platform users remain proactive to threats, stay up to date with new tactics used by cybercriminals, and take measures to protect against them.