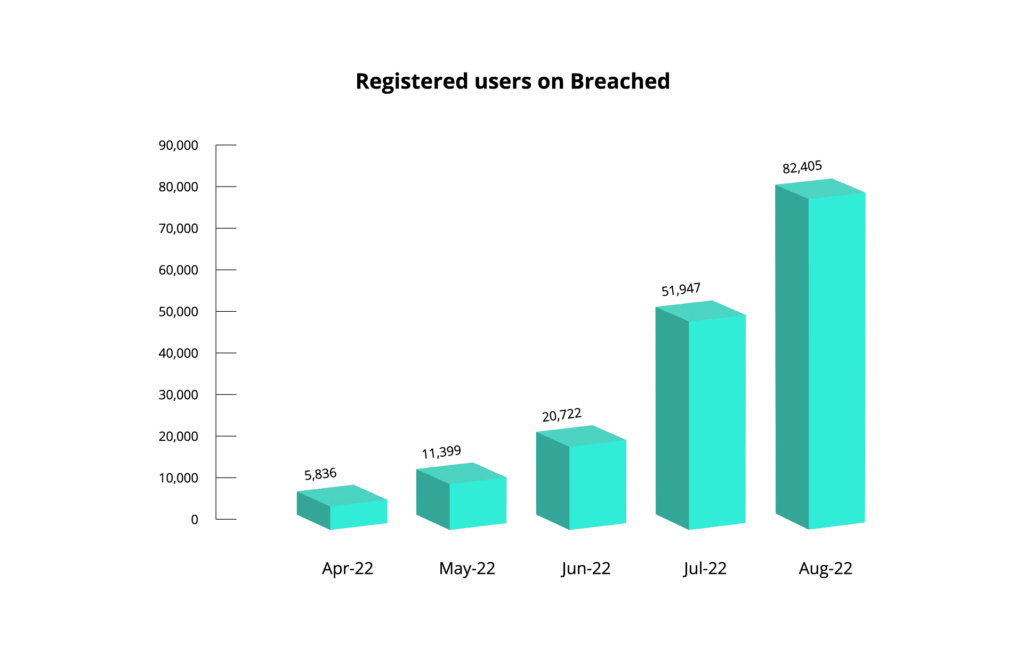On March 14, 2022, a new English-language cybercrime forum called Breached (also known as BreachForums) launched, as a response to the closure and seizure of the popular RaidForums. Breached was launched with the same design by the threat actor “pompompurin” as “an alternative to RaidForums,” offering large-scale database leaks, login credentials, adult content, and hacking tools.
In late January 2022, three prominent actors from RaidForums were arrested after the domain was seized – the administrator and creator of the forum “Omnipotent” and two other administrators, “Jaw” and “moot.” According to the US Department of Justice, the owner of RaidForums was Portuguese national Diogo Santos Coelho (aka Omnipotent), who was charged with conspiracy, access device fraud, and aggravated identity theft. Coelho and his partners are alleged to have designed the forum’s software and computer infrastructure and managed the forum, promoting database exchange.
After the closure of RaidForums, it was only a few weeks until the launch of Breached. And in the first six months of its existence, Breached has become the new platform for database exchange, attracting more than 82,000 registered users. KELA explored whether Breached has actually replaced RaidForums as the most popular database exchange site and analyzed the top actors’ activities and trends associated with the new forum.
How Breached has quickly filled the gap
Breached includes the types of content that appeared on RaidForums under the same categories including Cracking, Leaks, Marketplace, Tutorials, and Tech. Pompompurin said the motivation was to create a forum that includes the old RaidForums’ databases. In fact, pompompurin said, “all official databases from RaidForums [are] put on our own CDN (Content Delivery Network).” The most popular subcategory on Breached is Databases, which consists of dumps, in which credentials from various breaches are shared.
The Leaks section on Breached.
The first step was to initiate a large data leak collection, attracting users to the new forum. This was achieved by circulating old dumps that had been previously leaked on RaidForums. Pompompurin reshared them and responded to users who requested databases from the forum community.
Breached users have been encouraged to participate actively. As RaidForums, Breached introduced the concept of credits, which are rewards given to users for their contributions. Credits can be also bought and then used to spend on purchasing the content (usually databases) “locked” for a certain amount of credits. At first, Breached didn’t allow users to buy credits: the only way to “unlock” leaked databases was by posting new content in the same category and earning credits. This policy aimed to increase the engagement of the new forum and create a large database exchange. Then on March 29, 2022, pompompurin added the section for buying credits, expanding the possibilities for new users, who can buy credits to unlock content.
And it worked. In the first two weeks, the administrator pompompurin moved more than 100 databases shared by users to the site’s “official” section, which means that the databases will be saved on the forum servers, allowing access to old leaks anytime, and recognizing them as valuable. One of the known leaks reposted on Breached was from Wattpad, a social media reading site, which had been originally shared in July 2020 on RaidForums. On March 17, 2022, a threat actor reshared the Wattpad database, again publicizing the personal information of 270 million users.
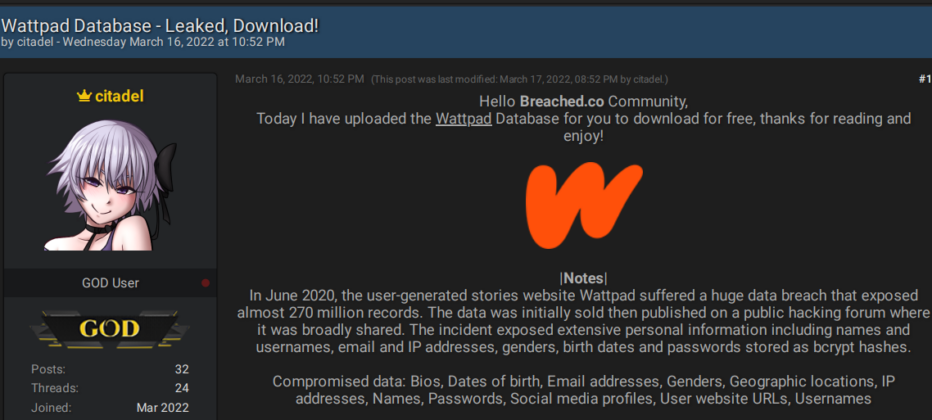
One of the biggest leaks on RaidForums has also now been circulated on Breached.
Apart from old RaidForums’ databases, other types of data leaks appeared on Breached. KELA had already identified that the Russia-Ukraine war has impacted the cybercrime landscape, which was also reflected in the new forum. Although Breached is an English-speaking forum, it appears that cyber warfare also contributed to the evolution of the database exchange on the forum. New dumps were shared on the forum, exposing data of Russian and Ukrainian companies. For example, on May 6, 2022, a threat actor shared a database of a Russian medical laboratory, which exposed 31 million credentials including names, email addresses, physical addresses, and phone numbers.
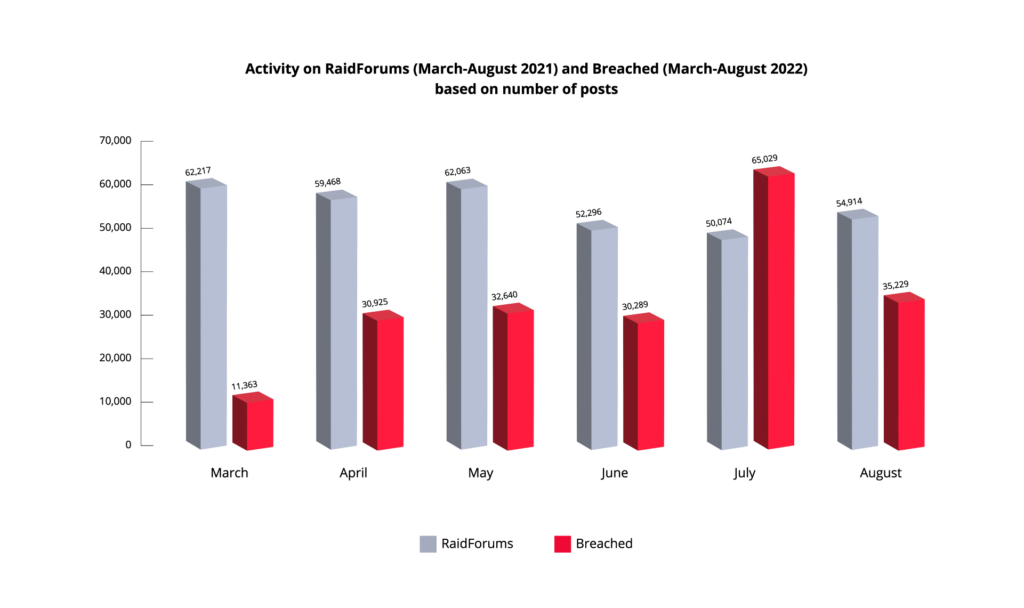
From March until August 2022, more than 82,000 members registered on Breached, 39% of whom have posted on the forum. Approximately 34,000 posts were created on the new forum per month. In comparison, during 2021, over 55,000 posts were published per month on RaidForums. In July 2022, there was a jump in the number of users registered on Breached. On June 24, 2022, there were over 20,000 registered users, while at the end of July the number more than doubled with almost 52,000 registered members.
As the number of users increased, so did the number of posts. Approximately 65,000 posts were shared in July alone, which shows that the new forum is stepping into RaidForums’ role.
The reason for the rising number of users and posts can be explained by several events that gained attention and received a high number of responses. These include a leaked video showing China planning to attack Taiwan and the release of a write-up explaining how to hack into RedPanda, a streaming data platform for developers.
Another big leak that gathered attention was a Chinese police leak. On June 28, 2022, a database allegedly belonging to the Shanghai National Police (SHGA) was first advertised for sale on a Russian/Chinese-speaking cybercrime forum RAMP by the user ChinaDan. The same day, the same offer was made on the Russian-speaking forum Exploit by an actor called AccessBroker.
The actor requested 10 BTC for the full database (around USD 200,000 at the time). On June 30, 2022, ChinaDan posted the same offer on Breached. The actor used the same Jabber across several forums, which proves these offers were made by the same actor. The database got a lot of attention from users of Breached, though the offer was soon deleted from the forum. Its popularity even caused the forum’s administrator to write a welcome message for Chinese users searching for the leak.
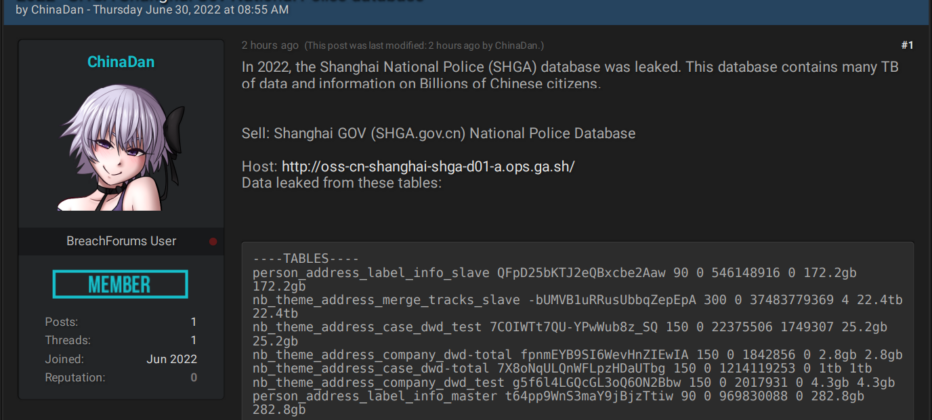
ChinaDan leaked the Shanghai Police database on Breached.
How Breached echoes RaidForums
It’s not just the design and data leaks from RaidForums that have appeared on Breached. It seems that some of the top actors of RaidForums adopted Breached as their new platform. Of the top 10 active actors on RaidForums (based on the number of messages), four continued being active on Breached under the same or very similar monikers. Two of those 10 moved to another Russian cybercrime forum named Rutor, while four were not identified on other underground forums.
For example, the threat actor “troubled” was the most active on RaidForums and he is operating now on Breached. First, the actor used the handle “Rainforest Shmainforest” and then changed to a name similar to the RaidForums one, “troubled2.” The actor is mainly buying databases and also responds to users’ posts. It seems that troubled2’s activity is currently much smaller than it had been on RaidForums.
The actor formerly known as troubled opened a new account on Breached.
Another instance: the threat actor “thekilob” was operating under the same handle on the new forum, and seemed to be well known among the user community. He quickly became the most active actor on Breached in the last six months. The number of posts (3,289) associated with this actor in these six months almost reached the number of messages posted by him in 18 months on RaidForums (3,451). However, since August 19, 2022, thekilob has been banned for bullying some members and selling credits to other users.
The threat actor thekilob began to post bullying comments on Breached, leading to his being banned.
The busiest actors on Breached: Some familiar monikers
It’s interesting to see who the most active actors are on Breached, and whether the prominent actors on RaidForums are among the top contributors to Breached. KELA observed that all the top 10 actors active on Breached had been registered on RaidForums, another sign that the new forum is a successor of the old one, attracting the same actors. Eight actors are operating under the same handles they used on RaidForums. Two have slightly changed their names. For example, the Breached actor “xDARKAx” used “Darka” on RaidForums.
Besides thekilob, mentioned above, there are other familiar names. The second most active user is “Dredgen Sun,” who has been active on Breached since its establishment and was also seen on RaidForums. It seems that this actor mainly comments on threads, not necessarily related to hacking activities. On March 18, 2022, this actor posted that he is happy to see the influx of RaidForums users “come back home,” referring to Breached as “home”. KELA identified that Dredgen Sun rebranded and operated under several handles on RaidForums, such as “Sunsingerlock” and “Sunsinger-Adept.” Sunsingerlock was the second most active moniker on RaidForums. On May 18, 2022, the actor claimed that “it’s good to have rebranding from now and then.”
Dredgen Sun is operating under a different moniker on Breached than he used on RaidForums.
The threat actor “Minori” is also very active on Breached, and served as a moderator for a short period. The actor is also active on such Russian-language forums as Exploit and XSS, mainly selling databases.
Pompompurin shared dozens of databases on RaidForums and continues on Breached, reposting old dumps made by other actors as well as sharing his own leaks. Recently, the actor shared a database of a Mexican bank, which apparently exposed data of 10 million users. The actor claimed that he bought the dump from another actor and leaked the data after getting a desist letter from a cybersecurity company regarding the data breach.
“Cod” seems to be very active on the new forum, compared with relatively little activity on RaidForums. On August 18, 2022, cod claimed that “the forum is basically a successor of RF [RaidForums]. We lack the amount of members RF had though.” The actor is interested in buying databases, and usually comments on posts that offer sensitive data such as databases, source code, and accesses.
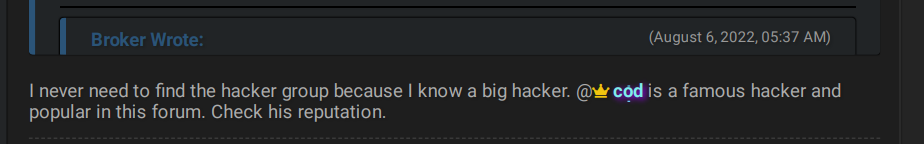
One actor claimed that cod is an experienced hacker.
Not all the actors post regularly on the forum but still seem to participate in meaningful activities, including stealing and leaking exclusive data. One of them is the threat actor named “desorden.” This actor was involved in big data breaches against Asian companies in 2021, affecting millions of customers worldwide. One of them was the data breach of the Taiwanese technology company Acer. In October 2021, the actor claimed to have stolen 60 GB of data from the company. The actor has been active on Breached since June 2022 and claims to have stolen data mainly from Asain companies, offering the databases for sale.
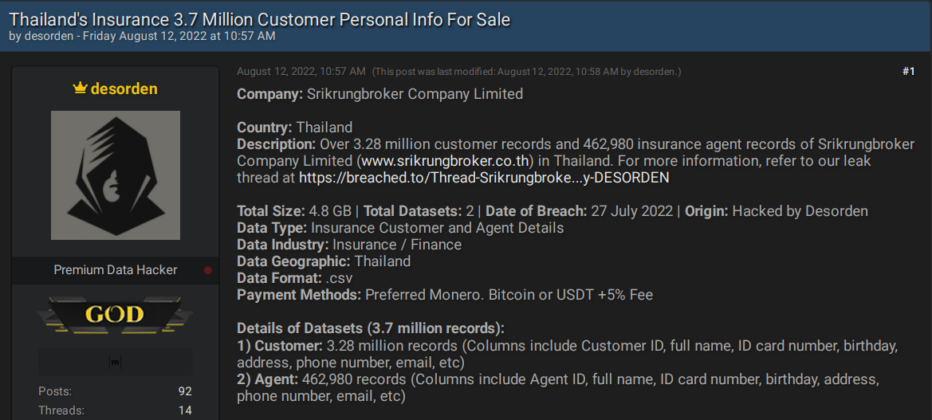
The threat actor desorden is back, hacking mainly Asian companies.
Another actor who was on RaidForums is LeakBase, who is operating the website LeakBase.cc, a site for searching data leaks of all kinds. Back in 2017, that site was also promoted on RaidForums. On Breached, the actor shares his leaks under several monikers, including Chucky, Chuckies, and Sqlrip (it is also possible these users are operated by the actor’s partners). The actor constantly shares hundreds of new SQL databases of shops and companies worldwide. Lately, the actor has started to regularly share collections of different databases.
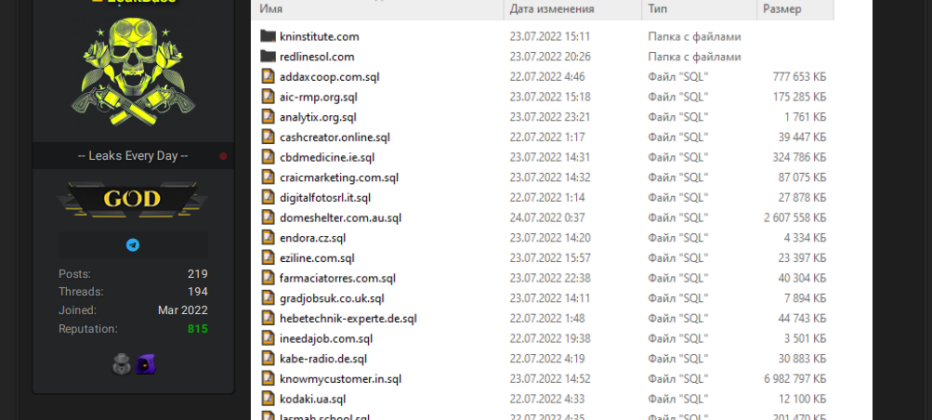
LeakBase has shared a collection of 50 databases on Breached.
Ransomware operators are also welcomed
Some ransomware groups have also been spotted on Breached. For example, the extortion group Everest also shares its leaks on Breached, while a threat actor allegedly associated with the Babuk ransomware affiliate program was interested in buying network accesses. The actor listed the same contact details as the ransomware group had in the past. In parallel, KELA identified several Initial Access Brokers (IABs) interested in selling network accesses to compromised companies.
KELA also observed a threat actor named “SolidBit” looking for ransomware affiliates experienced in getting initial access, performing lateral movement, and penetration testing tools like PsExec, Mimikatz, and Metasploit. The actor claimed that his team is deploying ransomware and that he is working on SolidBit version 2.0. On June 29, 2022, SolidBit also announced their ransomware-as-a-service (RaaS) program on Dread forum, promising to pay affiliates a share of 80% of a ransom. On its negotiation portal, SolidBit is imitating the LockBit ransomware logo and chat.
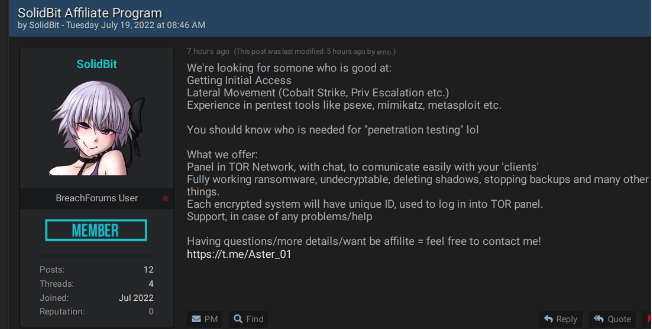
SolidBit’s affiliate program was introduced on Breached.
Sellers of ransomware builders and ransomware developers have also been active on the forum. On April 22, 2022, a threat actor shared a new version of Chaos ransomware (also known as Yashma). The actor has been also active on XSS under the moniker “chaos_exe,” providing updated versions of Chaos ransomware.
On July 5, 2022, the threat actor “Cerebrate” claimed to be the developer of Redeemer ransomware for Windows OS. The actor said that he has been running the ransomware for a year on the Dread forum and that users already have earned money for deploying it. The actor will provide a decryption key for getting a share of 20% of a victim’s total ransomware payment. Buying ransomware builders is also in demand by users on the forum.
Redeemer ransomware’s developer, Cerebrate, shares his malware.
On September 6, 2022, KELA observed the actor BN28 announcing a new ransomware-as-a-service (RaaS) operation called Garyk. The actor claimed their ransomware allows encrypting files very fast using the RSA 2048-bit algorithm. It will be provided to the operations’ affiliates to attack companies. After a victim pays ransom, the developer of the malware will get 20% of the ransom payment and will share a private decryption key. The affiliates will get a share of 80%.
Conclusion: Taking over where RaidForms left off
Breached is not only the successor of RaidForums, but in a very short timeframe has become a promising data leak marketplace. The increasing number of users, monthly posts on the forum, and the fact that known actors from RaidForums have chosen to join the platform shows pompompurin’s popularity and influence.
It also seems that ransomware operators are allowed to post, which expands the possibilities for a wide range of cybercriminals. KELA believes that the forum will continue gaining popularity in the next months and could become bigger and even more sophisticated than RaidForums.