Victoria Kivilevich and Sharon BittonWhile Australian mining companies are busy extracting natural minerals from their lands, cybercriminals are busy extracting sensitive information from mining companies’ infrastructures and employees. For more than a century, Australia’s economy has significantly benefited from the mining industry, with a particularly strong influence in the last decade. Employing over 260,000 people and being valued at more than 200 billion AUD, the mining industry is the primary contributor to the Australian economy, and in parallel under the spotlight for many cybercriminals. As growth of this industry continues to be evident, cybercriminals may be seen profiting more and more from the mining companies’ sensitive information. This industry, once relying almost solely on human work, has now evolved with the digital age to make use of technological support for day-to-day operations – naturally creating more opportunities for cybercriminals to exploit.
Australia’s mining industry comprises numerous companies, however for this research, we’ve decided to look into the top 5 companies to identify the interest of cybercriminals in this industry. The research consists of an overview of numerous cyber threats that we have identified, which if exploited correctly could cause significant risk to this industry. The highlights include:
KELA identified more than 91,000 leaked employee-credentials pertaining to the top 5 Australian mining companies, leaked through third party breaches over the last few years.
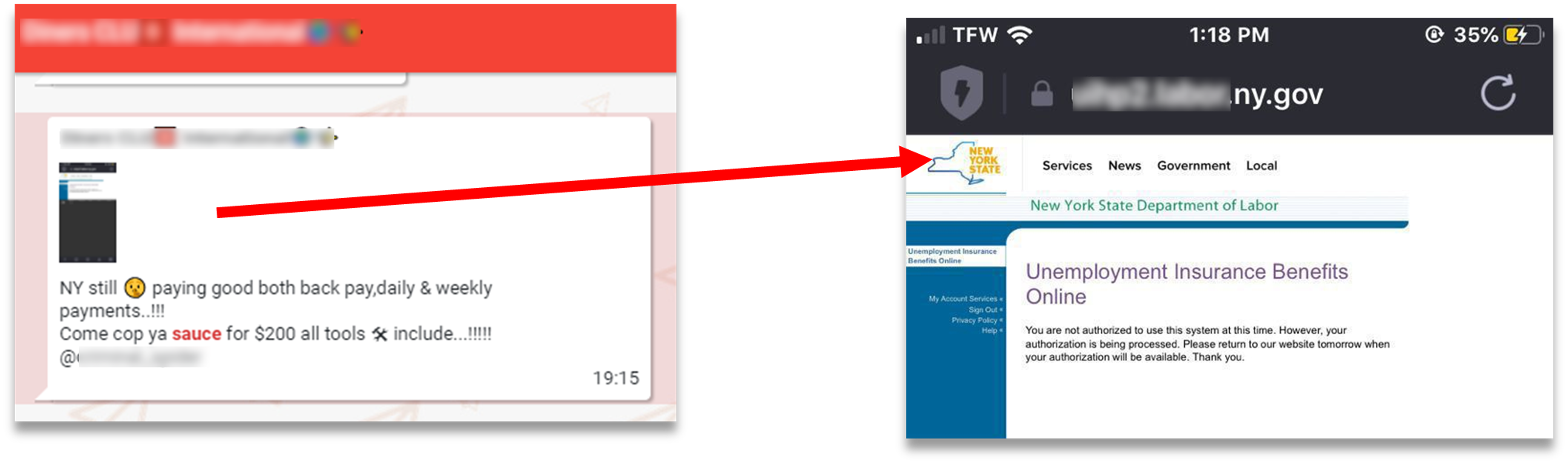
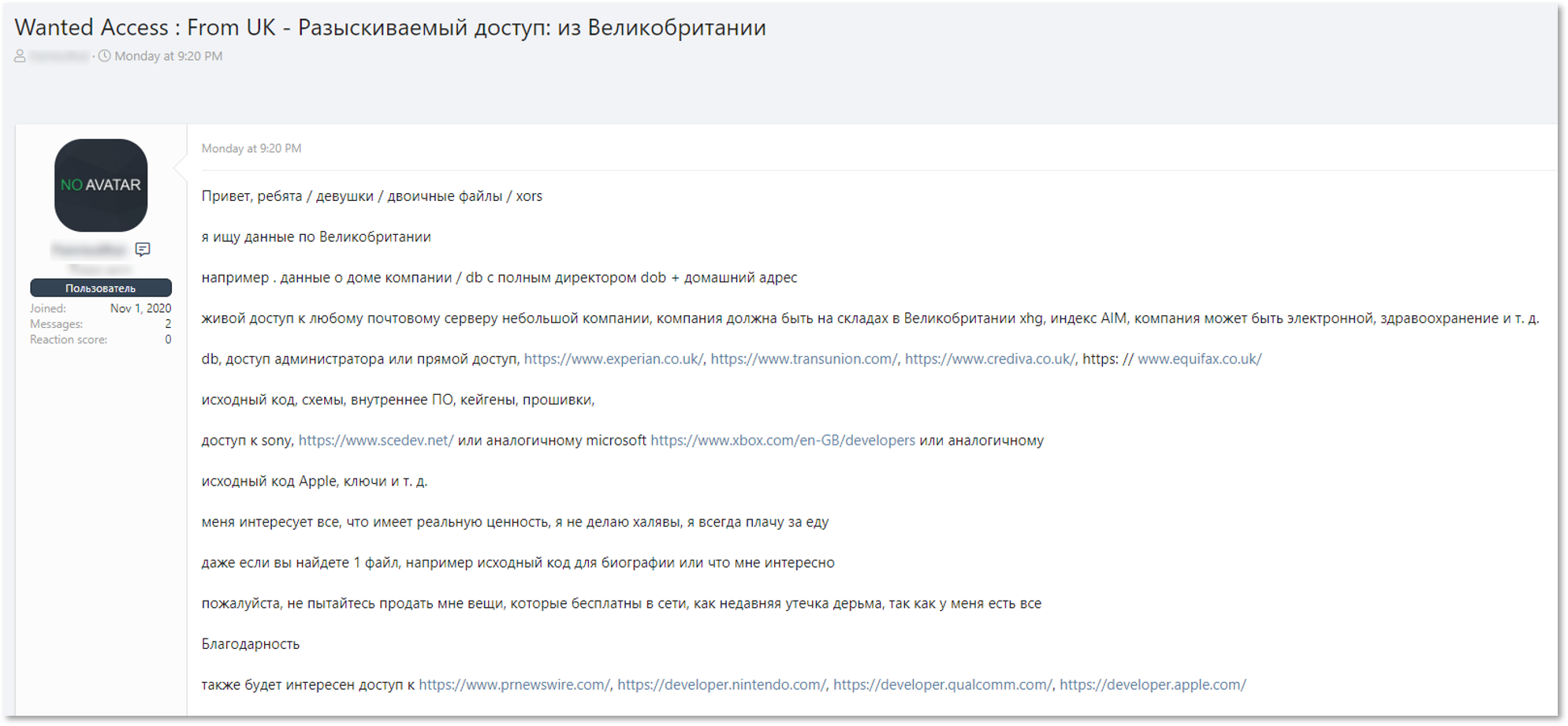
KELA discovered multiple compromised accounts related to employees in the Australian mining industry, which might provide access to sensitive corporate services.
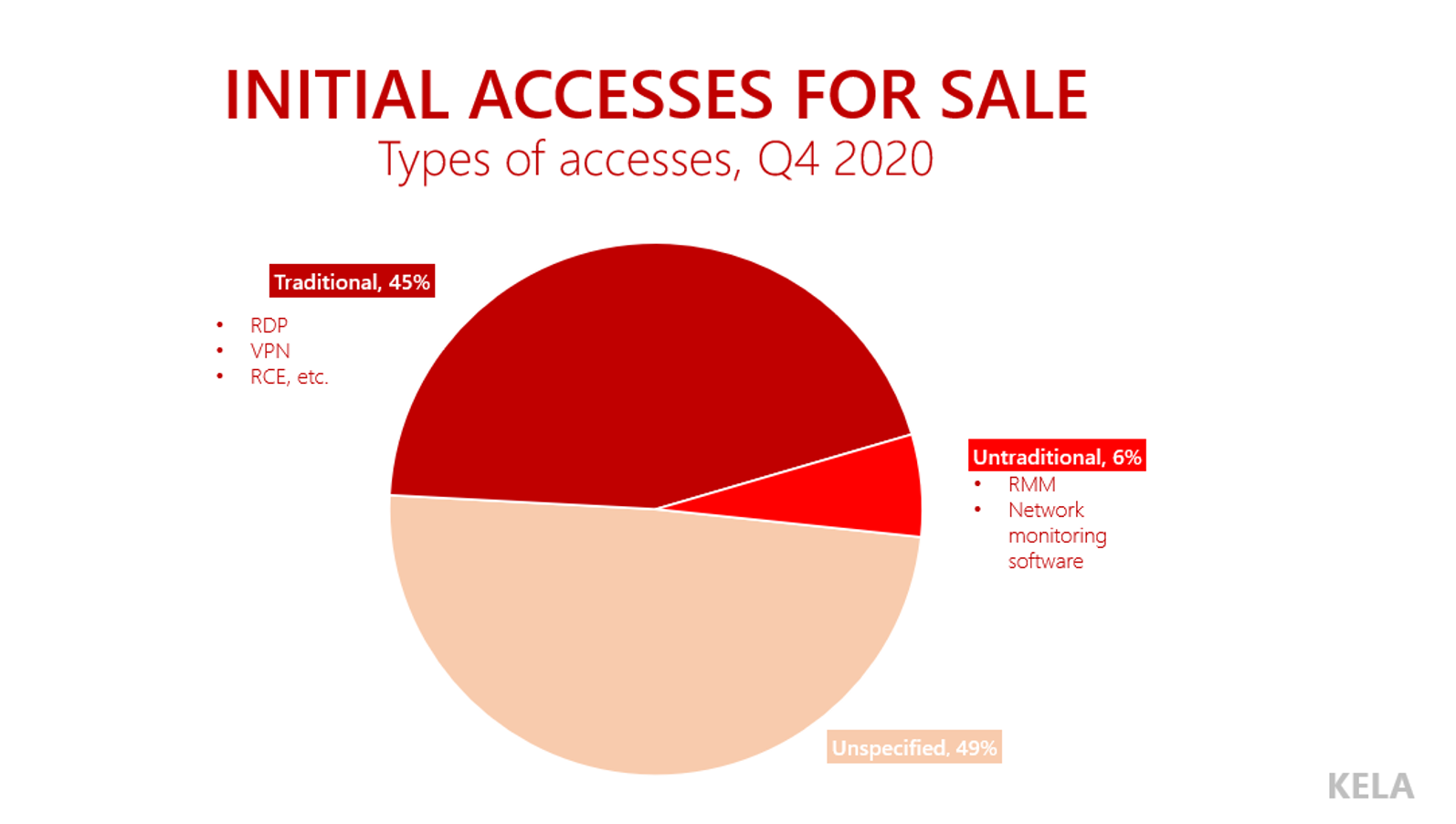
KELA observed numerous network vulnerabilities in the Internet-facing infrastructure of the top 5 companies in the mining industry.
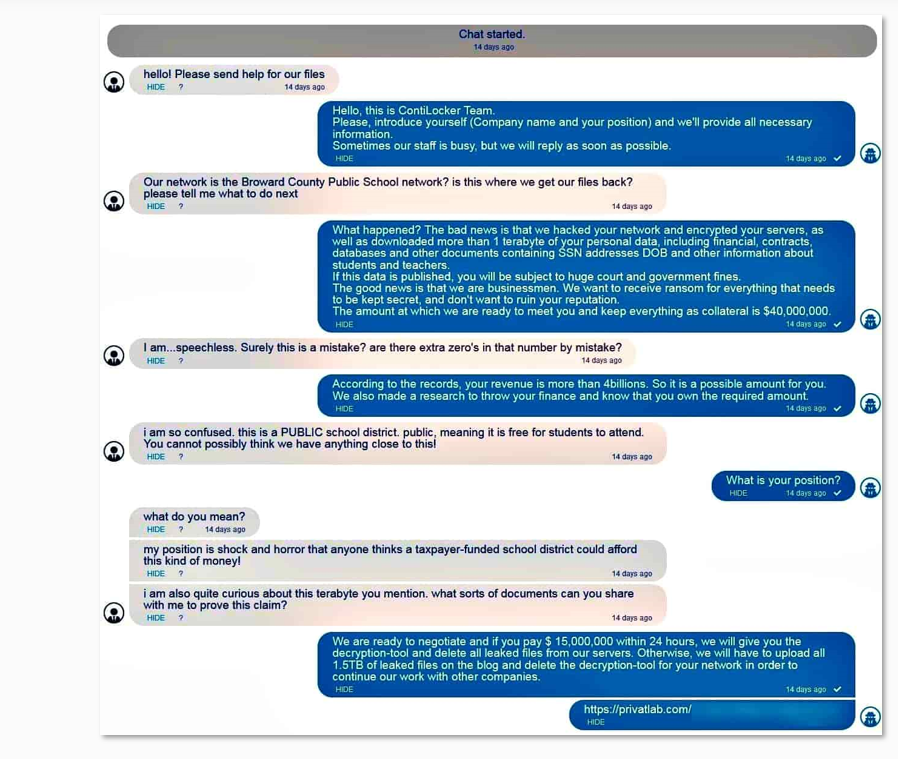
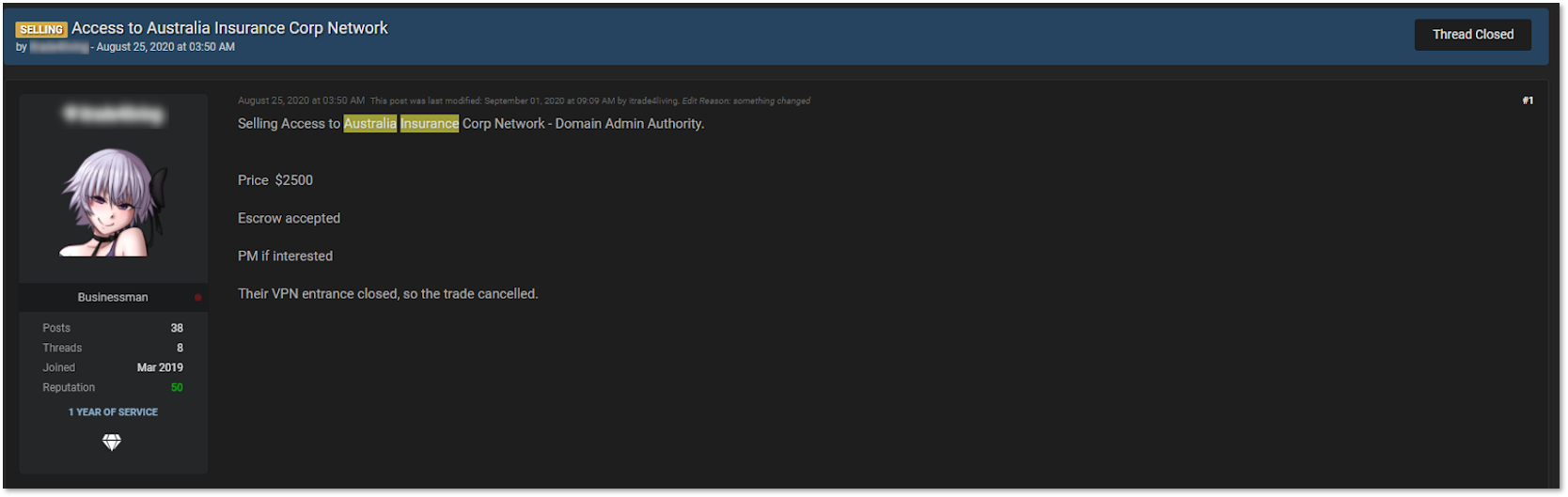
KELA detected a compromised network access listed for sale. Upon research, KELA identified that the victim is a company that provides services and stores sensitive data belonging to companies in the mining and energy sector in Australia.